CVE-2025-53770 & CVE-2025-53771: SharePoint Zero-Day Under Active Exploitation
CVE-2025-53770 is a live, high-severity threat that is already being exploited across global networks. This critical vulnerability in Microsoft SharePoint Server allows unauthenticated attackers to execute arbitrary code remotely, effectively handing them the keys to your infrastructure.
As of July 2025, over 85 SharePoint servers have reportedly been breached. And if your organization uses SharePoint 2016, 2019, or Subscription Edition on-premises, you could be next.
The risk increases significantly when CVE-2025-53771 is chained with CVE-2025-53770, enabling unauthenticated exploitation of on-premises SharePoint servers.
CVE-2025-53770 – Risk Analysis
Severity: CRITICAL
CVSSv3.1: Base Score: 9.8 CRITICAL
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Exploit available in public: Yes
Exploit complexity: Low
At its core, CVE-2025-53770 is a remote code execution (RCE) flaw that allows attackers to run code on a SharePoint server without needing credentials. The vulnerability arises from the unsafe deserialization of untrusted data, a long-standing weakness in many enterprise applications.
What makes this case so dangerous is that it bypasses previously issued patches. Earlier in May 2025, a chained exploit called ToolShell was demonstrated at Pwn2Own Berlin, combining CVE-2025-49704 (deserialization) and CVE-2025-49706 (auth bypass). Microsoft issued patches in July, but threat actors were quick to find a loophole. That led to CVE-2025-53770, effectively bypassing previous defenses.
How The Exploit Works
The attack begins with a crafted POST request sent to the vulnerable SharePoint endpoint:
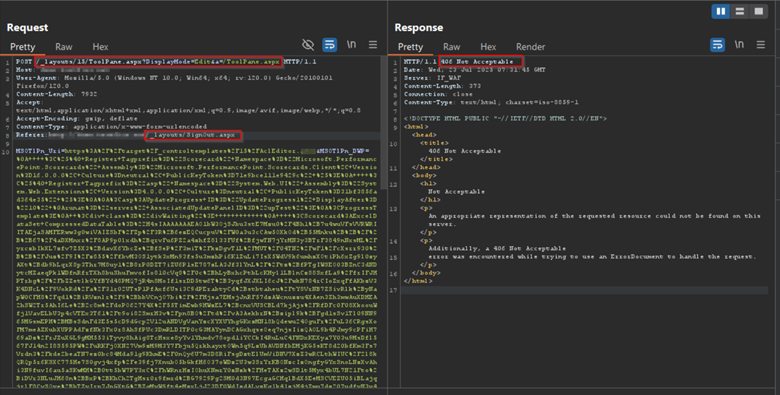
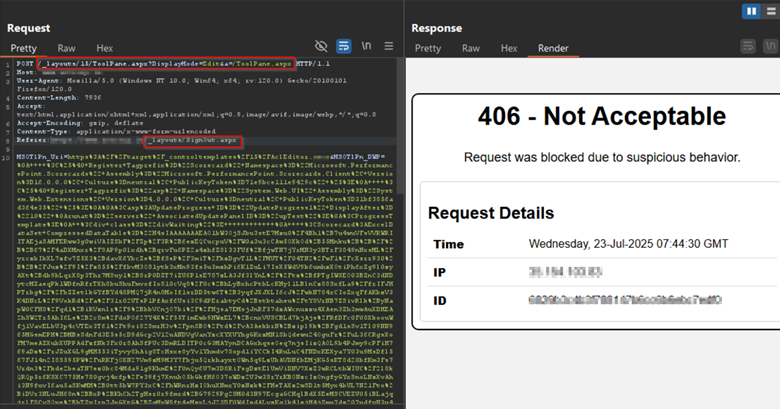
/_layouts/15/ToolPane.aspx
By manipulating request context headers (including Referer and proxy-related headers), attackers can trick the server into believing the request originates from a trusted location like:
/_layouts/SignOut.aspx
This spoofed header bypasses authentication mechanisms tied to session validation. The server proceeds to deserialize attacker-controlled payloads, resulting in code execution. Once inside, the attackers typically drop a web shell (spinstall0.aspx) in the layouts directory, giving them persistent access to the environment.
But it does not stop there. The next step is even more dangerous, they extract the server’s cryptographic machine keys: the ValidationKey and DecryptionKey. These allow attackers to forge authentication tokens and craft malicious payloads that appear completely legitimate.
CVE-2025-53771: The Missing Link in the SharePoint Zero-Day Exploit Chain
While CVE-2025-53770 enables unauthenticated remote code execution in on-premises Microsoft SharePoint Server, attackers are actively chaining it with CVE-2025-53771 to achieve full compromise.
CVE-2025-53771 is an authentication bypass vulnerability that allows attackers to spoof or bypass SharePoint authentication controls. On its own, this flaw may appear lower severity. In reality, it acts as the entry point that makes exploitation of CVE-2025-53770 trivial and reliable.
Security researchers have collectively referred to this chained exploitation technique as “ToolShell.”
How the ToolShell Exploit Chain Works
- CVE-2025-53771 (Auth Bypass)
The attacker sends crafted HTTP requests to specific SharePoint endpoints (commonly under /_layouts/15/) to bypass authentication entirely. - CVE-2025-53770 (Remote Code Execution)
Once unauthenticated access is gained, the attacker exploits the RCE vulnerability to execute arbitrary code on the SharePoint server. - Post-Exploitation
Attackers can deploy web shells, extract cryptographic secrets (including ASP.NET machine keys), pivot laterally, or establish long-term persistence.
Active exploitation has been observed in the wild, targeting internet-facing, on-premises SharePoint deployments across multiple industries.
Why CVE-2025-53771 Matters
Risk Analysis
Severity: MEDIUM
CVSSv3.1: Base Score: 6.5 MEDIUM
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:N
Exploit available in public: Yes
Exploit complexity: Low
CVE-2025-53771 carries a lower standalone severity score compared to CVE-2025-53770. That classification is misleading.
- CVE-2025-53771 removes the authentication barrier
- CVE-2025-53770 delivers full system control
Together, they enable unauthenticated, pre-auth server takeover. Treating either vulnerability in isolation understates the real-world risk.
If you patch only CVE-2025-53770 and ignore CVE-2025-53771, your SharePoint environment is still exposed.
What Makes CVE-2025-53770 & CVE-2025-53771 Dangerous
These vulnerabilities are most dangerous when exploited together as part of the ToolShell exploit chain.
-
Unauthenticated attack path – CVE-2025-53771 enables authentication bypass, allowing attackers to reach privileged SharePoint endpoints without valid credentials, while CVE-2025-53770 enables remote code execution.
-
Patch bypass capability – The exploit chain allows attackers to sidestep earlier July security updates, including protections released for CVE-2025-49704.
-
Key theft enables stealthy persistence – Attackers can extract ASP.NET machine keys and repeatedly return using signed payloads, without leaving obvious malicious files on disk.
-
Blends into legitimate SharePoint traffic – Exploitation occurs via standard SharePoint endpoints (such as
/_layouts/15/), making detection through logs and perimeter controls difficult. -
Broad, cross-industry targeting – Government, healthcare, financial services, and other sectors running internet-facing, on-premises SharePoint servers are actively targeted.
Real-World Exploitation
Active exploitation of this exploit chain was first reported on July 18, 2025. Within days, multiple security vendors and government agencies confirmed widespread scanning and exploitation activity.
CISA added CVE-2025-53770 to its Known Exploited Vulnerabilities (KEV) Catalog, urging organizations to patch immediately. Subsequent analysis revealed that attackers were chaining CVE-2025-53771 with CVE-2025-53770, significantly increasing exploit reliability and impact.
Threat actors continue to aggressively scan the internet for exposed SharePoint servers. Security researchers using FOFA identified over 200,000 potentially reachable SharePoint instances, representing a massive attack surface.
The method of attack reflects a strategic and targeted approach. It is not opportunistic malware; it is targeted exploitation aimed at persistence and stealth.
Microsoft’s Response
Microsoft responded by issuing emergency patches for supported versions of SharePoint:
- SharePoint Server 2019: Update KB5002754 (Build 16.0.10417.20037)
- SharePoint Subscription Edition: Update KB5002768 (Build 16.0.18526.20508)
- SharePoint 2016: Patch KB5002760 (Build 16.0.5513.1001)
These updates introduce more robust protections than earlier July patches, focusing on:
- Closing authentication bypass vectors (CVE-2025-53771)
- Hardening session validation
- Improving deserialization handling to prevent RCE (CVE-2025-53770)
Patching only one vulnerability is insufficient, both must be remediated together.
Mitigation Strategy: What To Do Now
If you are running on-premises SharePoint, immediate patching is non-negotiable. However, patching alone does not undo prior compromise.
After applying updates, organizations must:
-
Rotate ASP.NET machine keys – Generate new
ValidationKeyandDecryptionKeyvalues to invalidate stolen signing material. -
Hunt for web shells – Inspect the
/_layouts/directory and other SharePoint paths for suspicious or newly created.aspxfiles. -
Enable and verify AMSI integration – AMSI enables runtime inspection of scripts and payloads and is critical for detecting post-exploitation activity.
-
Investigate abnormal process chains, such as:
w3wp.exe → cmd.exe → powershell.exe -EncodedCommand
This process chain is a strong indicator of compromise and commonly observed in SharePoint post-exploitation scenarios.
CVE-2025-53770& CVE-2025-53771: AppTrana WAAP Coverage
AppTrana WAAP customers are protected from ToolShell exploitation (CVE-2025-53770 + CVE-2025-53771) from Day 0 through real-time threat intelligence and zero-day protection mechanisms.
Even when immediate patching is not feasible, AppTrana’s managed rulesets and continuous monitoring help block:
-
Authentication bypass attempts
-
Malicious SharePoint requests
-
Remote code execution payloads
This provides critical risk reduction during the patch window, when attackers are most active.
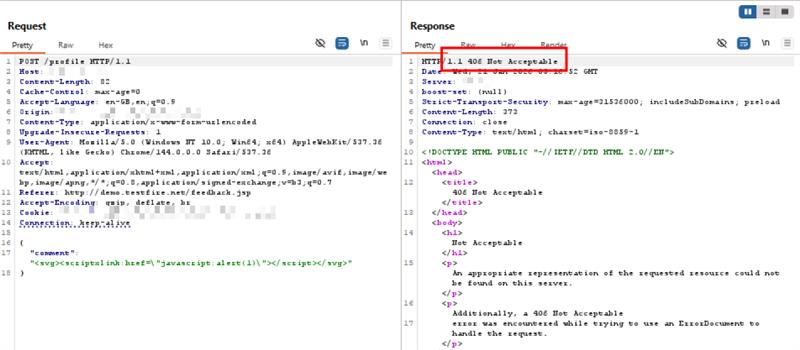
These PoC-driven screenshot(s) showcase AppTrana’s ability to identify and halt exploitation attempts effectively.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 July 23, 2025
July 23, 2025



