CVE-2025-11953 – Metro4Shell RCE in React Native Metro Server
A critical unauthenticated remote code execution (RCE) vulnerability has been identified in the React Native Metro development server, with nearly 3,500 exposed instances currently reachable on the public internet.
Tracked as CVE-2025-11953, also known as Metro4Shell, this flaw affects the Metro server used during React Native application build and testing workflows.
Although first disclosed in late 2025, CVE-2025-11953 has since progressed into active in-the-wild exploitation, with attackers targeting exposed Metro servers to execute malicious payloads and establish full system control.
In many real-world environments, Metro is exposed beyond localhost, unintentionally making the vulnerable endpoint accessible. This misconfiguration has transformed a development-only service into an active attack surface, making CVE-2025-11953 a high-priority risk for React Native deployments.
What Is CVE-2025-11953 (Metro4Shell)?
Risk Analysis
Severity: CRITICAL
CVSS v3.x Base Score: 9.8
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
EPSS Score: 0.00405
Exploit available in public: Yes
Exploit complexity: Low
Vulnerable Endpoint: /open-url
Impact: Arbitrary OS command execution
CVE-2025-11953 arises from improper input validation in the Metro server’s /open-url endpoint. The endpoint passes user-supplied input directly into an unsafe operating system invocation without adequate sanitization. As a result, attacker-controlled input can be interpreted as executable commands resulting in remote code execution (RCE) on the underlying system.
While EPSS predicts lower likelihood, real-world attacks show that developer-focused campaigns can evolve faster than statistical models. Confirmed exploitation activity highlights a gap between predictive risk scoring and observed attacker behavior, particularly in developer-focused attack campaigns.
CVE-2025-11953 – Affected Versions
CVE-2025-11953 affects the React Native Metro development server through the @react-native-community/cli npm package, which is responsible for starting and managing the Metro server during local development.
According to vendor and community disclosures, the vulnerability impacts @react-native-community/cli versions 4.8.0 through 20.0.0-alpha.2, where the vulnerable /open-url endpoint is present and exposed by default. These versions allow unauthenticated requests to reach the Metro server’s command invocation logic when the development server is accessible over the network.
The vulnerability has been addressed in version 20.0.0 and later, which include fixes to prevent unsafe command execution through the affected endpoint. Developers running vulnerable versions remain exposed unless they upgrade to a patched release or ensure that the Metro server is strictly bound to trusted interfaces and not reachable from untrusted networks.
Why Metro4Shell Poses a Serious Security Risk
The Metro development server is commonly used during local development and testing of React Native applications. By default, the server binds to all network interfaces rather than restricting access to localhost. This behavior can unintentionally expose the vulnerable endpoint to other systems on the same network.
In shared environments such as corporate offices, co-working spaces, or home networks, this exposure significantly increases attack surface. Because exploitation requires no authentication and no user interaction, developers may be compromised without any visible warning signs.
Successful exploitation allows attackers to gain control over developer machines, creating downstream risks such as:
- Theft of source code and proprietary logic
- Exposure of credentials, API keys, and tokens
- Access to internal repositories and CI/CD systems
- Potential pivoting into production environments
Metro4Shell Exploitation Observed in Active Attack Campaigns
Security researchers have confirmed that CVE-2025-11953 is being actively exploited to target developers. Observed campaigns focus on deploying multi-stage malware capable of persistence, command-and-control communication, and evasion techniques.
Attack activity has been documented across Windows, macOS, and Linux systems, with varying degrees of command execution flexibility depending on the operating system. These campaigns demonstrate a deliberate focus on development environments as an initial foothold.
CVE-2025-11953 – Mitigation and Remediation Guidance
Organizations and developers using React Native should take immediate steps to reduce exposure to CVE-2025-11953. The most effective remediation is to upgrade @react-native-community/cli to version 20.0.0 or later, which includes fixes addressing unsafe command execution in the Metro development server.
In addition to upgrading, it is important to ensure that the Metro server is not accessible from untrusted networks. Where possible, the development server should be explicitly bound to localhost to prevent unintended network exposure. This is particularly relevant in shared environments where multiple devices reside on the same network segment.
Development workstations should also be reviewed for overall security posture, including the handling of credentials, API keys, and access tokens that may be present during local development. Monitoring for unexpected outbound connections or anomalous network activity originating from developer machines can help identify potential compromise.
Development environments often have access to source code, internal repositories, and deployment systems. As a result, they should be treated as sensitive assets and secured with the same level of attention as production-facing systems.
AppTrana WAAP Coverage for CVE-2025-11953
AppTrana by Indusface has provided protection against exploitation attempts associated with CVE-2025-11953 from day zero. The platform applies built-in inspection and enforcement controls to detect and block malicious requests targeting vulnerable development server behavior in React Native environments.
By stopping exploitation attempts before they can reach developer systems, AppTrana helps reduce the risk of unauthorized command execution and downstream compromise during active exploitation and remediation periods. This ensures an added layer of protection for exposed development workflows while patching and configuration changes are being implemented.
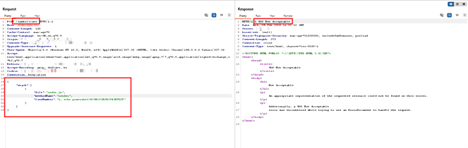
Screenshot showing malicious request activity associated with CVE-2025-11953, detected and blocked by AppTrana WAAP.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 February 6, 2026
February 6, 2026



