What Your Web App Security Had Been Missing?
Today, new-age companies are looking at unsettling questions like- How do we prevent application data breaches and downtime?
With the rising number of security lapses, the question is inevitable. While many companies understand the importance and need for proper web app security infrastructure, they do not know where to look for it. After all, which new age business has time to abandon their key business activity and focus entirely on security?
That is exactly the issue that we look to solve with our recent Total Application Security launch on the Amazon Web Services Marketplace.
If you are not aware of the Indusface Total Application Security market launch, you can read about the launch here. In this post, I’m going to talk about innovations that Total Application Security brings with this release and how it will benefit your business.
Most Powerful Vulnerability Detection
Total Application Security offers you the most sophisticated scanning solution that includes not only automated testing but also complex manual penetration testing. It is conducted by certified web app security experts who test the application with a potential attacker’s mindset. Pen testing not only helps in finding complex vulnerabilities but also finds gaps in business logic, which are specific to every application.
These vulnerabilities are made available in the portal with sufficient information so that you can assess the impact and prioritize them.
Perform a free application scan now with AWS 14-day free trial.
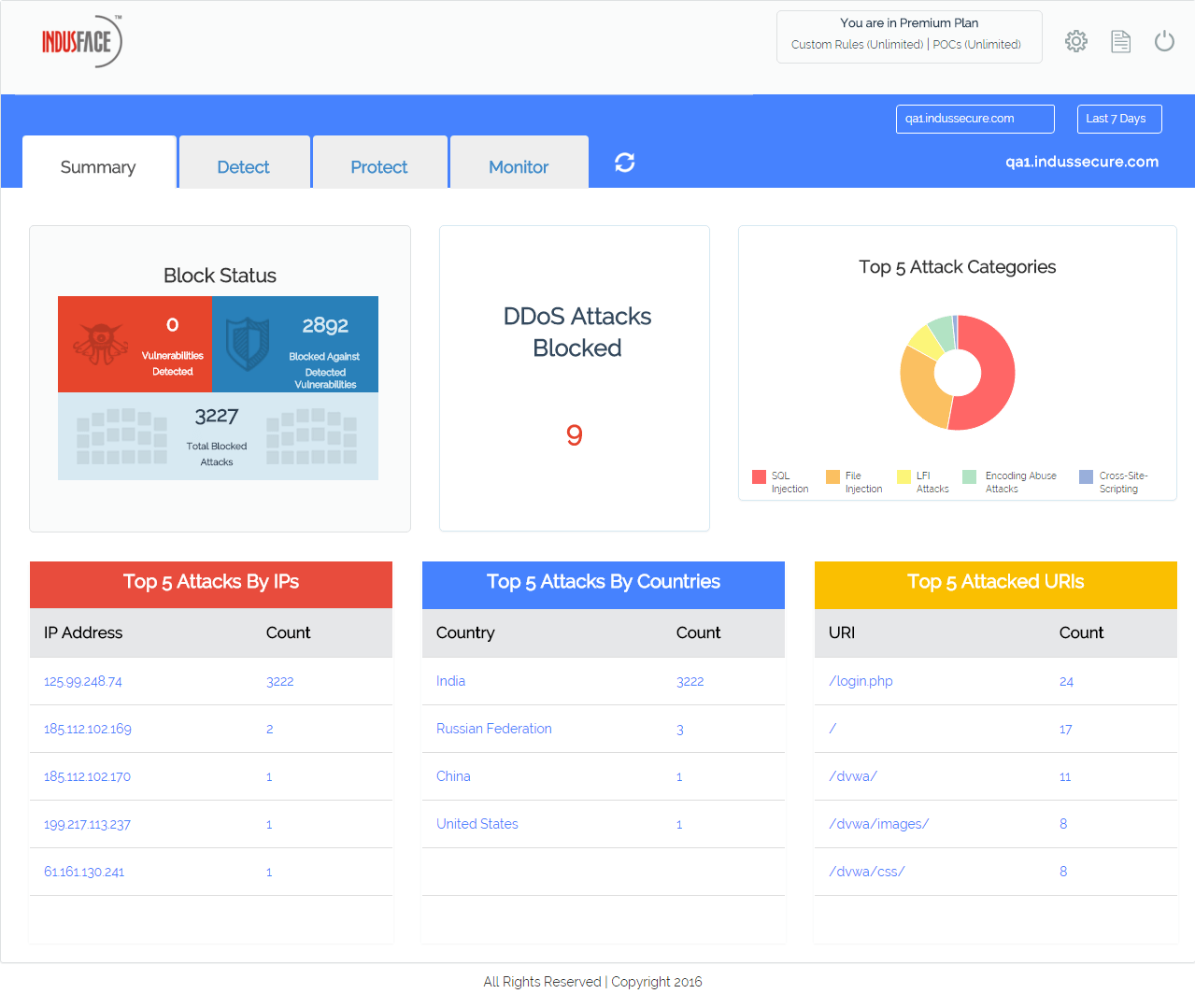
Adaptive and Dynamic Web Application Protection
In an ideal web app security world, detected vulnerabilities should be patched proactively. But, how much of that actually happens? Old applications, resource shortage, or negligence, whatever the reasons are, you cannot afford hackers exploiting vulnerabilities to get your data.
Web application firewall becomes an integral part of the security infrastructure here. But, what good is a WAF if it’s working on a decade-old rule set of identifying and blocking threats?
Total Application Security offers your business an adaptive and dynamic web application firewall that not only works on a core ruleset but also custom rules developed by our security experts. For example, your app is attacked from Nigeria and you don’t have any business in Nigeria. You can completely block that country. You can block it at any time.
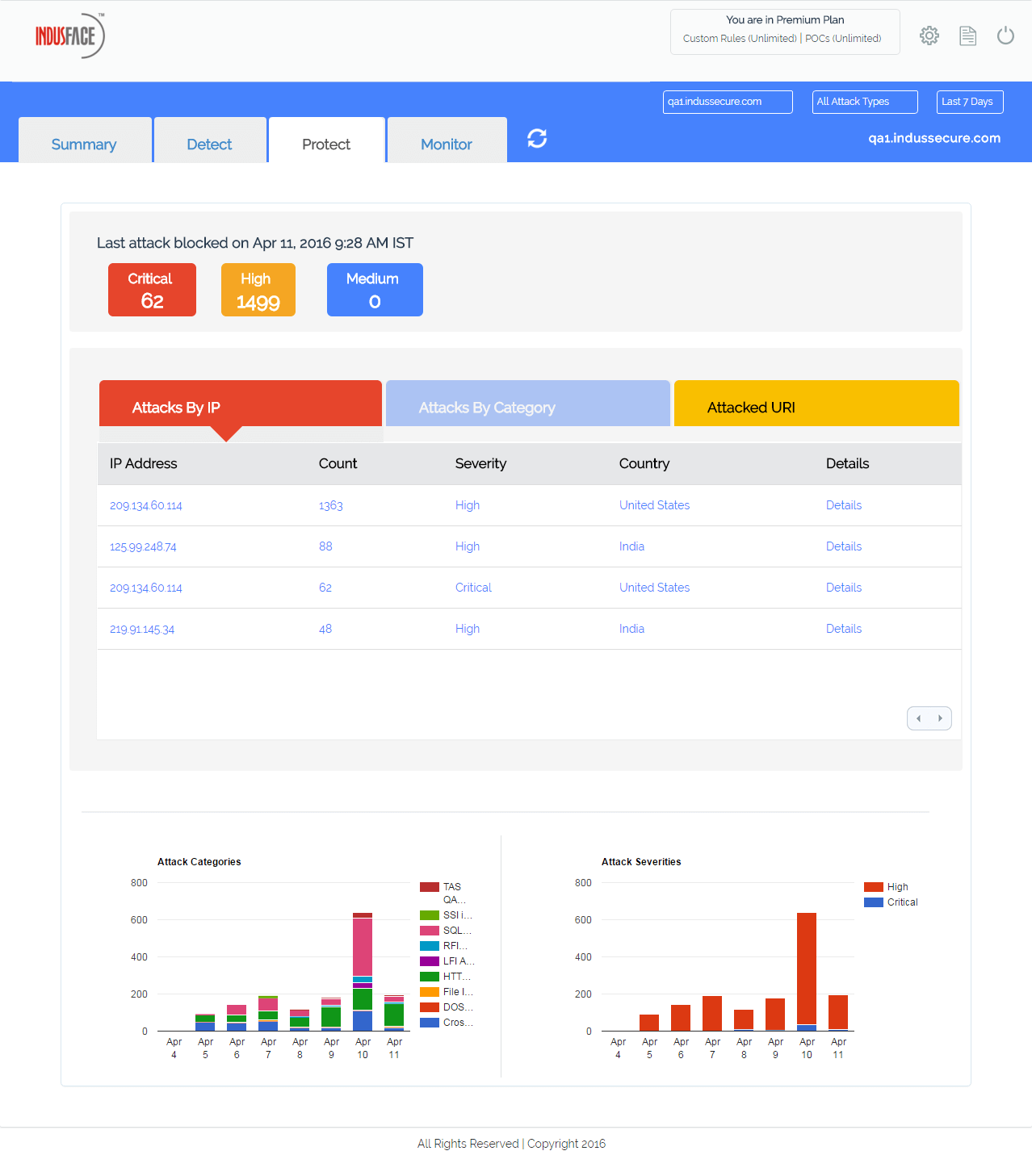
Some of the vulnerabilities are a little more complex and require application-specific rules. Our security experts will review the vulnerabilities that require custom rules and develop rules manually to protect those vulnerabilities. These security experts are like your extended team working for protecting your application 24×7. They monitor traffic identify proactively to identify new attack patterns and come up with remediation.
Protect your website from DDoS and app attacks with a 14-day Free Trial on the AWS Marketplace.
Total Application Security is equally efficient against application-layer DDoS attacks. There is actually no way to automatically detect and stop a distributed denial-of-service attack. When there is a traffic surge, how would you differentiate real traffic from fake ones? Last year, the DDoS world record was broken with a 500Gbps attack. That kind of attack can crash the average application before administrators can even react.
Total Application Security analyses traffic 24×7 to look for DDoS patterns. Our experts manually identify these risks and make sure that your application doesn’t suffer downtime.
Managed Monitoring Advantage
How about having a managed security team working always for you? Total Application Security includes continuous monitoring and supports of your applications. It is like having an extended security team that studies suspicious activity, ensures that genuine users are never blocked, and creates custom rules.
The managed security team also includes penetration-testing experts who detect complex vulnerabilities with the application framework. And you can request penetration testing whenever you want.
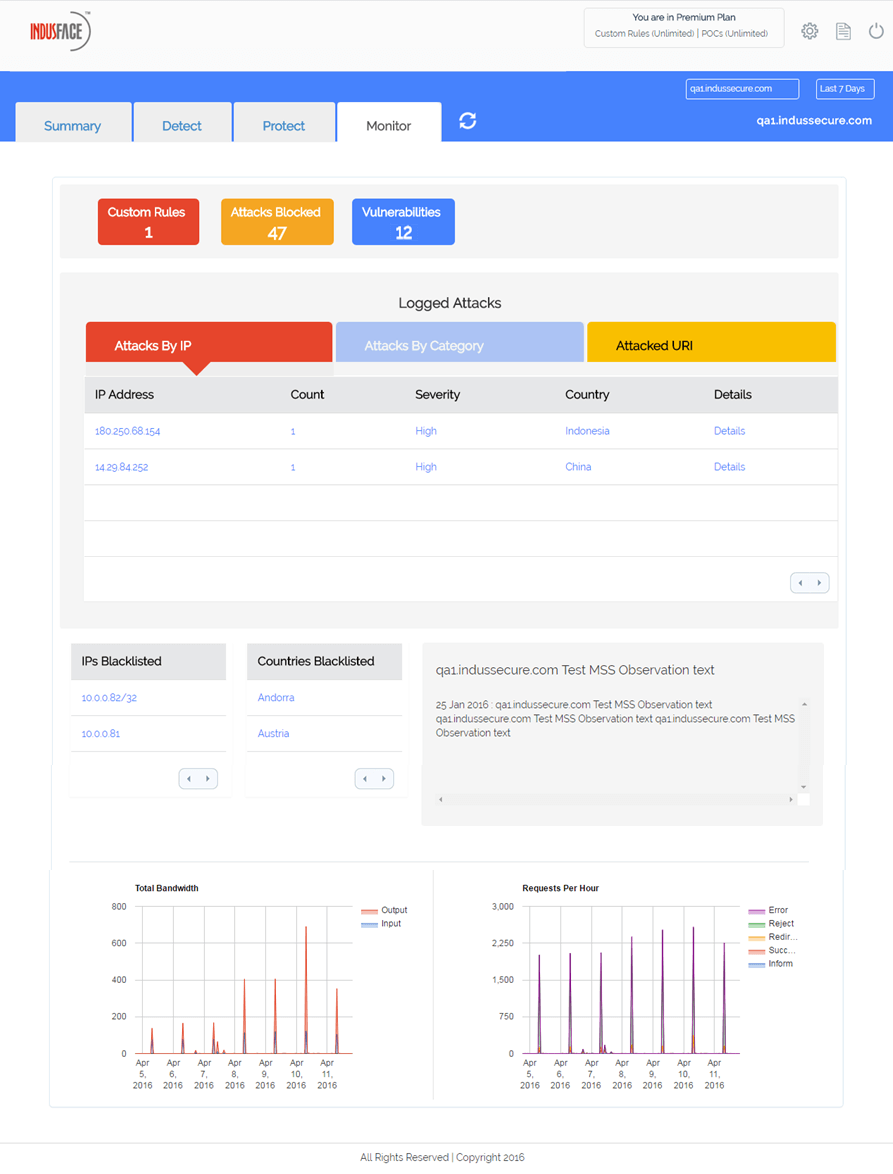
If you are unsure how a certain detected vulnerability can be exploited for attacks, they can demonstrate that too with proof-of-concept (POC). Of course, this also includes monitoring application traffic to identify and mitigate distributed denial-of-service attacks And other application attacks.
Complete Application Security Control
Finally, one of the most important things about Total Application Security is control. It’s not like outsourcing application security in a way that you do not know what’s happening.
In fact, the Total Application Security Portal ensures that you know exactly what kind of vulnerabilities have been detected. You can understand the risk imposed by those vulnerabilities by reviewing the vulnerabilities by severity. You can identify the number of critical, high, and medium vulnerabilities.
The Portal also keeps you updated on a number of attacks, their origin, and what you can do about these issues. You can block countries or IPs, request scans or pen testing, download reports, and get expert recommendations here. You are also updated about the remediation actions taken by the Indusface Managed Security Services team.
Take our start 14-day free trial now for scanning, protection, and managed security.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 April 26, 2016
April 26, 2016






