5 Most Shared Application Security Posts in 2016
How was your 2016? We know that for most businesses it was a little rough, especially on the cybersecurity front. As more and more companies prepare for cloud and digital domains, there is growing ambiguity on application security. Unfortunately, 2016 didn’t help. In fact, it was the weakest year in history with close to a thousand reported data breaches.
Number of Data Breach Incidents-Yearly
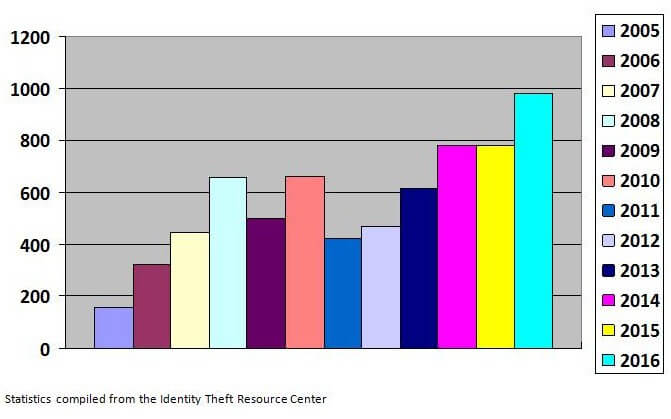
As we predicted last year, in our trend prediction blog post, ransomware, app DDoS and loss of Personally Identifiable Information (PII) created the most trouble for big and small businesses. We hope that this article helped our clients and readers close weak points well in advance.
Not that we look back, our research articles reached thousands of people worldwide helping them overcome security challenges. So, we bring you a list of the top five most shared posts that will prove valuable in the coming year too.
What Is SQL Injection?
How can a 17-year old vulnerability still top the OWASP Top 10 list? Given that SQL Injection is accountable for most data breaches, this post provides valuable information on understanding the vulnerability, its impact and ways to get rid of it.
OWASP Part 4: Mobile Application Risks
The last part of our popular OWASP Top 10 Series juxtaposed user-friendliness with security loopholes. It helped business owners look for loopholes in their mobile apps and close the gaps with the help of their team.
Google URLs Found Vulnerable to Open Redirect
What can a simple vulnerability such as Open Redirection do? Should businesses and customers really worry about them? This post sheds light on how invalidated redirects and forwards cause damage to business reputation and loss of business.
6 Things You Should Know About DDoS Attacks
Application layer DDoS attacks cause massive damage, especially by taking the website down for hours or days. This research article shatters many perceptions of Layer 7 attacks and how they affect every company that has a website.
3 Steps to Stop Hackers
Is there a simple guide for application security? Bookmark this one for all your questions on finding security loopholes, fixing them instantly, and stop DDoS attacks.
Stay tuned for more relevant and interesting security updates. Follow Indusface on Facebook, Twitter, and LinkedIn


 January 31, 2017
January 31, 2017






