Reducing Scan Noise: False Positive Mitigation Strategies for MSSPs
For Managed Security Service Providers (MSSPs), efficiency is everything. Every minute wasted chasing false positives is time that could have been spent on genuine threats, client communication, or platform improvement. Yet, excessive scan noise continues to plague many MSSPs, overloading SOC teams, distorting dashboards, and eroding client confidence.
Reducing scan noise is not just about tuning tools; it is about building a continuous validation framework that ensures accuracy, trust, and operational scalability.
To understand how automation, AI-driven rule validation can help MSSPs scale managed security services profitably, explore the MSSP Managed WAF Playbook.
The Cost of False Positives for MSSPs
For Managed Security Service Providers (MSSPs), false positives hit to profitability, SLA compliance, and client trust. When scanners, WAFs, or SIEM systems generate thousands of benign alerts, the real cost is not in detection; it is in wasted triage cycles, delayed remediation, and regulatory exposure.
1. Operational Overload Across Multi-Tenant Environments
Each benign alert consumes analyst time and adds to queue fatigue. In a multi-tenant MSSP model managing dozens or even hundreds of client environments, false positives multiply operational overhead exponentially.
- Every non-actionable alert can take 30–90 minutes of analyst time to investigate and close.
- Repetitive noise from vulnerability scanners, intrusion systems, and application firewalls diverts focus from genuine incidents.
- The result: increased mean time to response (MTTR), higher staffing needs, and reduced profitability per client as revalidation tests end up being ad hoc and prevent resource planning.
Operational Reality: A 40% false-positive rate can consume up to half of an MSSP’s SOC bandwidth, driving analyst fatigue and increasing cost-to-serve metrics across contracts.
2. SOC Analyst Fatigue and Burnout
False positives do not just slow operations; they erode human trust in automation.
When analysts encounter too many inaccurate alerts, they begin to subconsciously deprioritize incoming notifications, leading to alert fatigue.
- Continuous validation of benign alerts causes disengagement, frustration, and burnout.
- When every third alert turns out to be harmless, analysts may start ignoring legitimate incidents, a dangerous behavioral pattern known as “alert blindness.”
- Over time, this reduces detection accuracy and increases the likelihood of missing true positives, particularly zero-day or multi-vector attacks.
False positives directly reduce SOC productivity, leading to slower detection of real compromises and potentially allowing lateral movement or data exfiltration to go unnoticed.
3. SLA Violations and Compliance Gaps
For MSSPs bound by Service Level Agreements (SLAs), excessive scan noise can have contractual and regulatory consequences.
Every minute spent triaging a false positive is time not spent mitigating real threats, delaying patching timelines and exposing clients to compliance risks.
- For example:PCI DSS (Requirement 6.2): Mandates that known vulnerabilities be patched within 30 days of identification. False positives delay validation and patch cycles, risking non-compliance.
- ISO 27001 (Annex A.12.6.1): Requires prompt remediation of technical vulnerabilities. Inaccurate alerts inflate response timelines and increase audit findings.
Noise-induced delays can result in audit failures, SLA penalties, and potential regulatory fines if vulnerabilities remain unresolved beyond mandated timelines.
4. Client Confidence Erosion
MSSP relationships are built on trust and clarity. Clients expect proactive insights, not alert dumps.
When they receive reports riddled with unverified or repetitive alerts, confidence drops and competitors look more appealing.
- False positives make an MSSP appear reactive rather than intelligent.
- Clients question whether their provider’s tools are properly tuned or if they are paying for inefficiency.
- Excessive noise in vulnerability reports undermines the perceived value of managed services.
In client reviews and renewal discussions, excessive alert noise is one of the top three reasons cited for MSSP churn.
MSSP Strategies for False Positive Reduction and Scan Noise Elimination
Effective false positive reduction requires a strategic blend of technology optimization, process automation, and intelligent data correlation. The goal is not just to silence noise, it is to create a security operations framework where every alert has meaning, priority, and context.
1. Client-Aware Scanning Configurations
False positives often stem from generic scanning setups that fail to reflect individual client environments. Each organization operates with a distinct mix of web applications, APIs, frameworks, and security requirements. When scans are not aligned to these specifics, harmless activity or known components can easily be flagged as potential risks.
For MSSPs managing multiple tenants, reducing this baseline noise begins with creating client-aware scanning profiles, where scan behavior, alert thresholds, and suppression rules are customized to reflect each client’s real-world environment.
Indusface WAS MSSP Edition supports this approach through flexible whitelisting options that allow analysts to fine-tune detections per tenant:
- Whitelist alerts or plugins: Analysts can exclude recurring or known benign findings directly from the dashboard, minimizing repetitive false positives.
- Bulk whitelisting for efficiency: Multiple alerts or plugins can be whitelisted at once, saving time during large-scale reviews.
- Criticality control: Vulnerabilities with Critical severity are intentionally non-whitelistable, ensuring that serious vulnerabilities are never suppressed accidentally.
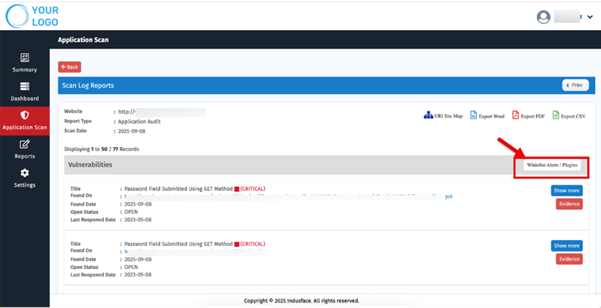
By leveraging these configuration options, MSSPs can eliminate noise generated by trusted or low-risk components, allowing analysts to focus on genuine vulnerabilities. The result is a cleaner, more accurate vulnerability feed and significantly faster triage cycles across tenants.
MSSPs evaluating advanced scanning or vulnerability management tools can refer to our guide here.
2. Proof-Based Verification for Exploit Validation
In MSSP operations, one unverified alert can trigger hours of unnecessary analysis. The key to eliminating scan noise is proof-based validation, confirming which vulnerabilities are truly exploitable before escalation.
Indusface WAS MSSP Edition provides this through automated proof-of-concept (PoC) verification and Managed Security Team validation for every vulnerability identified. When a scan detects a potential weakness, the system automatically replays the exploit in the live client environment to verify real-world impact.
From the MSSP dashboard, analysts can:
- Click on the total vulnerability count for a specific scan to open detailed listings.
- Select “Show More” to view complete exploit evidence, including tampered requests and responses generated by the PoC tool.
- Access the “Evidence” section to understand exactly why a vulnerability was marked valid, supported by payloads, logs, and replay data.
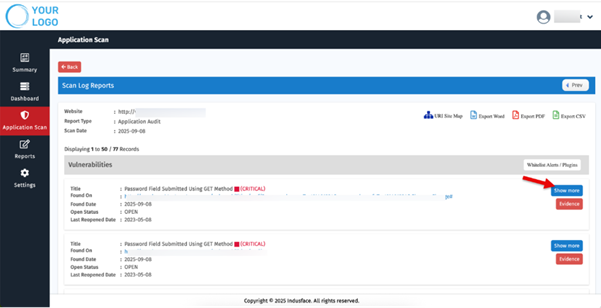
Each finding is verified by the Indusface Managed Security Team, ensuring zero false positives before it appears in client reports. This combination of automated and human validation eliminates the noise that plagues most vulnerability scans.
3. Contextual Threat Intelligence Integration
Even validated alerts can lose relevance without context. MSSPs handle diverse client profiles across industries and geographies, making it vital to understand whether an alert represents a genuine threat or routine activity.
By integrating contextual threat intelligence, MSSPs can distinguish between benign and malicious behaviors:
- Real-time threat feeds: Cross-check alert sources against global IP reputation data to recognize scanning engines, research crawlers, or benign testing networks.
- IOC correlation: Match detected indicators with known attacker infrastructure to confirm intent.
- Geo-behavioral analytics: Detect anomalies that deviate from a client’s usual user geography or login timeframes.
Within Indusface WAS MSSP Edition, these contextual insights are deeply embedded into the DAST scanning workflow. The platform’s AI-driven engine continuously correlates vulnerability data with live threat intelligence to assess the real-world relevance and exploitability of every finding.
This integration enables MSSP analysts to go beyond simple detections, they receive intelligent, risk-based prioritization backed by real-time context and AI analysis. Instead of static vulnerability lists, analysts get actionable insights highlighting the alerts that truly demand attention. The result is higher detection accuracy, faster triage, and significantly reduced scan noise across all client environments.
4. AI-Driven Correlation Across Tenants
At scale, MSSPs manage hundreds of clients and thousands of assets, often encountering similar vulnerabilities across environments. Without intelligent correlation, security teams waste valuable time analyzing repetitive findings and validating duplicate alerts.
Traditional scanners often miss hidden or dynamic areas of web applications, leading to incomplete visibility and redundant detections.
Indusface WAS’s AI-Crawler overcomes this limitation by learning from previous scans and intelligently grouping UI elements. This optimization:
- Enhances crawl speed, accuracy, and efficiency by minimizing redundant actions.
- Uncovers previously inaccessible application areas, improving overall scan depth and coverage.
- Reduces repeated or irrelevant detections by understanding context and user flows.
For MSSPs, this translates into cleaner vulnerability data, fewer duplicate alerts, and faster validation cycles across client environments.
5. Continuous Feedback and Proof-Driven Tuning Loops
Eliminating scan noise is not a one-time setup, it is a continuous feedback loop that evolves with every scan. Indusface WAS MSSP Edition embeds this principle into its workflow through evidence-backed tuning, analyst feedback integration, and adaptive learning. This cycle of validate → learn → refine ensures that your MSSP platform grows smarter, quieter, and more accurate with every iteration.
Built specifically for MSSPs, Indusface WAS provides centralized visibility across multiple tenants, role-based access control, and automated reporting, enabling teams to efficiently manage, validate, and act on findings at scale. Its AI-driven insights continuously refine detection logic, helping analysts maintain a consistently low false-positive rate and high client confidence.
Empower your MSSP operations with precision.
Explore how Indusface WAS MSSP Edition helps you eliminate false positives, streamline client management, and deliver validated security at scale.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.
Frequently Asked Questions (FAQs)
False positives occur when a scanner or monitoring tool flags benign activity as a security threat, wasting analyst time and resources.
High false-positive rates lead to operational inefficiency, alert fatigue, SLA risks, and potential erosion of client trust.
Strategies include fine-tuning scanning rules, proof-based verification, threat intelligence integration, AI-powered alert correlation, and continuous feedback loops.
DAST scanners like Indusface WAS leverage AI-driven analysis along with human validation to verify exploitability and eliminate noise.
Yes. By reducing wasted labor and operational overhead, MSSPs can scale services efficiently while maintaining client satisfaction and margins.
Clear, actionable reports that separate true threats from false positives, along with proof-based verification, help clients understand and trust security outcomes.

 October 16, 2025
October 16, 2025



