CVE-2025-68613: Critical n8n RCE Vulnerability Enables Full Server Compromise
A critical remote code execution (RCE) vulnerability has been disclosed in n8n, a popular open-source workflow automation platform widely used to orchestrate business processes, SaaS integrations, and internal automation pipelines.
Tracked as CVE-2025-68613, the vulnerability carries a CVSS score of 9.9 (Critical) and allows authenticated attackers to execute arbitrary system-level code on vulnerable n8n instances. Successful exploitation can result in complete server takeover, unauthorized data access, workflow manipulation, and potential lateral movement across connected systems.
With over 100,000 internet-exposed instances identified as potentially vulnerable, this vulnerability represents a priority-zero risk for organizations running self-hosted or embedded n8n deployments.
What Is CVE-2025-68613?
Risk Analysis
Severity: CRITICAL
CVSSv3.1: Base Score: 9.9 CRITICAL
Vector: CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H
Exploit available in public: Yes
Exploit complexity: Low
EPSS Score: 0.22%
CVE-2025-68613 is a remote code execution vulnerability in n8n’s workflow expression evaluation engine.
Under certain conditions, expressions supplied by authenticated users during workflow configuration are evaluated in an execution context that is not sufficiently isolated from the underlying runtime. This lack of sandboxing allows crafted expressions to escape the intended execution scope and execute arbitrary code with the privileges of the n8n process.
Once exploited, attackers can:
- Execute OS-level commands
- Access or exfiltrate sensitive workflow data and credentials
- Modify or destroy automation logic
- Pivot into adjacent systems and networks
The vulnerability affects a wide range of n8n releases, increasing real-world exposure:
All versions starting from 0.211.0 and prior to:
- 1.120.4
- 1.121.1
- 1.122.0
These versions include many long-lived and stable builds commonly used in production and self-hosted deployments. n8n has released patches that properly address the sandbox isolation vulnerability in the following versions:
- 1.120.4
- 1.121.1
- 1.122.0
Organizations that previously applied partial mitigations or configuration-based workarounds must still upgrade. Earlier fixes did not fully remediate the underlying sandbox escape condition.
CVE-2025-68613 – Technical Root Cause
The vulnerability stems from insufficient isolation in n8n’s expression evaluation mechanism.
n8n workflows allow users to define expressions that dynamically process data during execution. These expressions are intended to run inside a controlled sandbox. However, in vulnerable versions:
- User-supplied expressions can be evaluated in a context that exposes the underlying JavaScript runtime
- The sandbox boundary can be bypassed
- Arbitrary code can be executed with the same permissions as the n8n service
This effectively turns workflow configuration privileges into remote command execution capabilities.
While authentication is required, no elevated system privileges are necessary beyond the ability to create or edit workflows permissions that are commonly granted in multi-user or DevOps-oriented deployments.
Exploitation Path: How CVE-2025-68613 Leads to Full Compromise
Initial Access via Legitimate Workflow Permissions
Exploitation begins when an attacker gains authenticated access to an n8n instance with permissions to create or edit workflows. This access level is commonly granted to developers, DevOps engineers, automation owners, and integration partners. In many environments, these permissions are shared broadly to support collaboration, increasing exposure in the event of credential compromise or insider misuse.
Injection of a Malicious Workflow Expression
The attacker embeds a malicious expression into a workflow definition. n8n’s expression language is intentionally powerful, allowing dynamic data handling, conditional logic, and runtime transformations. In vulnerable versions, this flexibility becomes an attack vector.
Sandbox Escape During Expression Evaluation
When the workflow is validated or executed, the malicious expression is evaluated in a context that is not sufficiently isolated. Under specific conditions, the expression escapes the intended sandbox and gains access to the underlying JavaScript runtime.
Arbitrary Code Execution on the Host
Once sandbox isolation is bypassed, the attacker can execute arbitrary code with the privileges of the n8n process. This may include:
- Executing OS-level commands
- Accessing environment variables and secrets
- Reading or writing files
- Making outbound network connections
Persistence and Lateral Movement
From this foothold, attackers can establish persistent control by modifying workflows, planting backdoors, or abusing stored credentials. Because n8n often integrates with cloud services, databases, and CI/CD systems, the instance can be leveraged to pivot laterally into connected environments.
Key Risk Factor:
No additional user interaction is required, and no elevated system privileges are needed beyond workflow access, making exploitation realistic in operational environments.
CVE-2025-68613 – Mitigation and Remediation Guidance
Organizations should upgrade immediately to one of the following patched versions:
- 1.120.4
- 1.121.1
- 1.122.0
Upgrading is the only complete and reliable fix, as it enforces proper isolation during expression evaluation. Security teams should confirm versions across all environments, including development, staging, disaster recovery, and embedded deployments.
If immediate upgrades are not feasible, apply the following short-term controls to reduce exposure:
- Restrict workflow creation and editing permissions to fully trusted users only
- Review existing workflows for unusual or overly complex expressions
- Deploy n8n in a hardened environment, including:
- Minimal operating system privileges
- Restricted filesystem access
- Network segmentation to limit lateral movement
- Strict outbound (egress) network controls
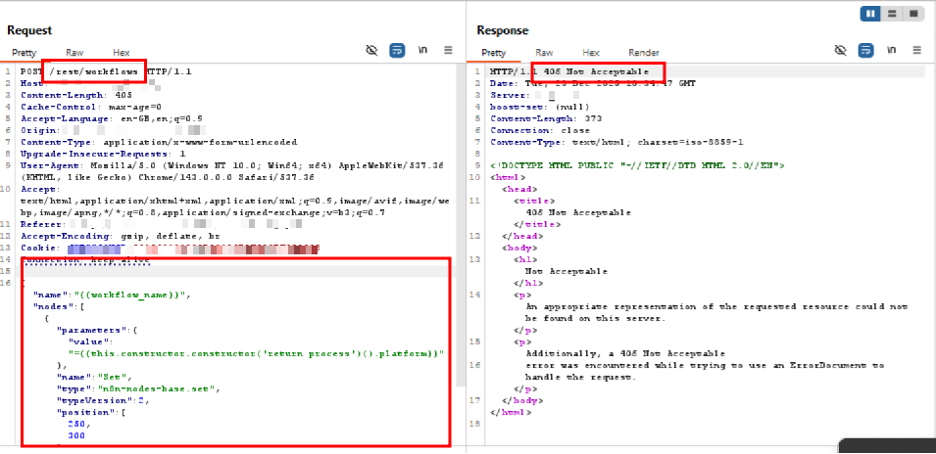
How AppTrana WAAP Blocks n8n Expression Injection Exploitation Attempts
AppTrana WAAP provides immediate protection during patch windows by detecting and blocking malicious workflow expression payloads designed to exploit CVE-2025-68613 in n8n.
The vulnerability abuses n8n’s workflow expression evaluation mechanism, where attacker-controlled expressions escape sandbox boundaries and execute arbitrary code within the n8n runtime. AppTrana mitigates this risk by applying deep, intent-based inspection across inbound workflow configuration requests and execution-triggering API calls.
Example: Malicious Workflow Expression Blocked by AppTrana
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 December 24, 2025
December 24, 2025



