CVE-2025-66675: Apache Struts DoS Vulnerability Leads to Disk Exhaustion
A newly disclosed denial-of-service vulnerability, CVE-2025-66675, affects a wide range of Apache Struts 2 versions and poses a serious availability risk for applications that handle file uploads. While the EPSS score is 0.05%, indicating a low probability of exploitation in the next 30 days, the vulnerability still represents a high availability risk for exposed and unpatched environments.
Apache Struts is a widely used Java web application framework, and this vulnerability impacts both legacy and newer deployments still running vulnerable releases.
What Is CVE-2025-66675?
Risk Analysis
Severity: HIGH
CVSSv3.1: Base Score: 8.2 HIGH
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:H
Exploit available in public: No
Exploit complexity: Low
EPSS Score: 0.05%
CVE-2025-66675 is a denial-of-service (DoS) vulnerability caused by incomplete cleanup of temporary files created during multipart/form-data request handling. Multipart requests are commonly used for file uploads, and Apache Struts automatically creates temporary files to process these requests.
Due to a vulnerability in the cleanup logic, these temporary files are not reliably removed once request processing completes. When multipart requests are repeatedly sent, the temporary files accumulate on disk, steadily consuming available storage space.
How CVE-2025-66675 Is Exploited
The exploitation process is straightforward and requires no authentication or special permissions. An attacker can continuously submit multipart upload requests containing files or large form data. Each request causes Apache Struts to create temporary files that are not fully cleaned up.
Over time, this behavior leads to disk exhaustion. Once disk space is depleted, the affected application may stop responding, crash, or fail to generate logs. In severe cases, the entire server becomes unstable, resulting in prolonged service outages.
Because multipart handling is enabled by default in many Struts deployments, even applications that do not actively rely on file uploads may still be exposed.
The vulnerability affects a broad range of Apache Struts releases, highlighting its long-standing nature:
- Struts 0.0 through 2.3.37
- Struts 5.0 through 2.5.33
- Struts 0.0 through 6.7.4
- Struts 0.0 through 7.0.3
CVE-2025-66675 was issued to correct incomplete affected-version information in CVE-2025-64775, specifically adding Struts version 6.7.4 to the impacted range. Both CVEs describe the same underlying vulnerability and should be addressed together.
CVE-2025-66675: Why This DoS Vulnerability Is High Risk
Although CVE-2025-66675 does not allow remote code execution or data manipulation, its availability impact is significant. The attack is remote, unauthenticated, and low complexity, making it easy to automate and difficult to detect early without proper monitoring.
For organizations running customer-facing or business-critical applications, disk exhaustion attacks can cause operational disruption, SLA violations, and reputational damage. The risk is further amplified in environments where legacy or end-of-life Struts versions are still in use.
Mitigation and Remediation Guidance
- Upgrade immediately to a patched version of Apache Struts to fully resolve the multipart file cleanup vulnerability.
- Fixed versions: Apache Struts 6.8.0 and Apache Struts 7.1.1
- Prioritize upgrades for internet-facing and business-critical applications that support file uploads or multipart request handling.
- If immediate upgrading is not possible, implement temporary risk-reduction measures, including:
- Isolating file upload temporary storage to a dedicated, size-limited directory to prevent system-wide disk exhaustion
- Monitoring disk usage closely and setting alerts for abnormal growth patterns
- Apply additional safeguards where feasible:
- Enforce rate limiting on multipart upload requests
- Disable file upload functionality if it is not required by the application
AppTrana Coverage for CVE-2025-66675
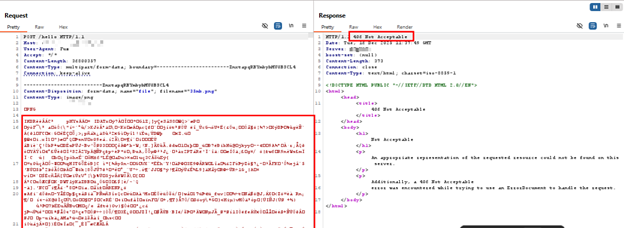
AppTrana WAAP provides out-of-the-box protection against exploitation attempts targeting CVE-2025-66675 in Apache Struts. AppTrana WAF detects and blocks malicious multipart request patterns designed to abuse file upload handling and trigger disk exhaustion conditions.
Example of multipart upload abuse associated with CVE-2025-66675, blocked by AppTrana WAAP protections.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 December 17, 2025
December 17, 2025



