React After React2Shell: New RSC Vulnerabilities Expose DoS and Source Code Risks
The disclosure of React2Shell (CVE-2025-55182) triggered a rapid patching effort across the React and Next.js ecosystem. However, deeper inspection of React Server Components (RSC) in the aftermath revealed additional vulnerabilities in adjacent code paths. These vulnerabilities pose serious operational and security risks.
Notably, CVE-2025-55183 and CVE-2025-55184 carry EPSS scores of 1.064% and 4.543% respectively, signaling a higher likelihood of real-world exploitation compared to most newly disclosed vulnerabilities. Together with CVE-2025-67779, they demonstrate how residual risk can persist even after primary patches are applied.
Why Follow-Up Vulnerabilities Matter After a Major Disclosure
Large-scale vulnerabilities like React2Shell trigger intense scrutiny across the surrounding codebase. This often leads to the discovery of:
- Previously overlooked logic vulnerabilities
- Incomplete fixes
- Secondary attack paths that were not initially weaponized
The React team has acknowledged that these follow-on disclosures are a natural outcome of deeper inspection, not failed remediation. However, for defenders, this means the risk window often extends well beyond the first patch cycle.
CVE-2025-55184: Denial-of-Service via RSC Deserialization
Risk Analysis
Severity: HIGH
CVSSv3.1: Base Score: 7.5 HIGH
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
Exploit available in public: No
Exploit complexity: Low
CVE-2025-55184 is a denial-of-service vulnerability rooted in how React Server Components process serialized data sent from the client. Specifically, the vulnerability arises from unsafe handling of structured input in the RSC Flight protocol, which allows specially crafted payloads to introduce cyclical Promise references.
An attacker can send a specially crafted RSC request that causes the server runtime to repeatedly unwrap nested Promises. Instead of resolving cleanly, the runtime enters an infinite loop or event-loop lockup. Once this condition is triggered, the server becomes unresponsive and stops processing legitimate requests.
The attack is fully remote and unauthenticated. It does not depend on custom server logic, misconfiguration, or privileged access. In many default React and Next.js deployments, the vulnerable code paths are reachable simply because RSC support is enabled.
From an attacker’s perspective, this creates a low-cost, high-impact availability attack. A single malformed request can effectively take an application offline. Repeated exploitation can force frequent restarts, degrade performance, or cause extended outages, especially in autoscaled environments where crashing instances trigger resource churn.
While CVE-2025-55184 does not allow an attacker to execute arbitrary code, its impact on availability makes it highly disruptive. For production systems, particularly those serving customers or processing transactions, this kind of denial-of-service can be just as damaging as a breach.
CVE-2025-67779: When the Initial Fix Is Not Enough
Risk Analysis
Severity: HIGH
CVSSv3.1: Base Score: 7.5 HIGH
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H
Exploit available in public: No
Exploit complexity: Low
Following the release of patches for CVE-2025-55184, researchers identified that the initial fix did not fully address all exploitable conditions. This led to the disclosure of CVE-2025-67779, which restores the same denial-of-service behavior under certain configurations.
This has two important implications:
- Teams that patched early may still be vulnerable
- Additional upgrades are required to fully eliminate the DoS risk
Teams that patched quickly after React2Shell may believe they are protected, when in reality they remain exposed to a different but equally disruptive attack vector. CVE-2025-67779 makes it clear that upgrading once was not sufficient. A second round of updates is required to fully close the denial-of-service risk.
CVE-2025-55183: Source Code Disclosure via Server Functions
Risk Analysis
Severity: MEDIUM
CVSSv3.1: Base Score: 5.3 MEDIUM
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N
Exploit available in public: No
Exploit complexity: Low
While CVE-2025-55184 and CVE-2025-67779 focus on availability, CVE-2025-55183 introduces a confidentiality risk through source code disclosure. This vulnerability affects React Server Functions under specific conditions involving argument handling and type coercion.
In vulnerable implementations, a Server Function may accept arguments that are implicitly coerced into strings. If those arguments are not strictly validated, an attacker can manipulate them to reference another Server Function. When the runtime processes that reference and implicitly calls .toString(), the source code of the referenced function may be returned in the response.
This behavior can expose internal implementation details that were never meant to be visible outside the server. In real-world applications, this could include proprietary business logic, internal API structure, or even secrets if they are embedded directly in code.
Although exploitation depends on specific conditions, modern React applications often rely heavily on Server Functions and shared utilities. As applications grow in complexity, the likelihood of hitting one of these unsafe patterns increases, especially in large codebases maintained by multiple teams.
How These CVEs Connect Back to React2Shell
These vulnerabilities are not independent discoveries. All of them:
- Originate from the React Flight protocol
- Involve server-side handling of attacker-controlled structured data
- Were discovered during post-React2Shell audits
React2Shell demonstrated how unsafe deserialization could lead to full RCE. The follow-up CVEs show that even when code execution is blocked, availability and confidentiality remain at risk.
This underscores a broader security lesson: once a protocol boundary is weakened, multiple exploit classes often emerge.
Affected Versions
Applications using React Server Components, especially those built on Next.js App Router, remain the most exposed. Many teams assume that not explicitly using server logic reduces risk, but framework defaults can still expose vulnerable code paths. Any application running React versions from 19.0.0 through 19.2.2 is affected, even if it has already patched for React2Shell.
To fully remediate all known RSC vulnerabilities, applications must be upgraded to React 19.0.3, 19.1.4, or 19.2.3. Anything below these versions leaves at least one exploitable condition open.
Defense Beyond Patching: Reducing the Exposure Window
In reality, patching is never instantaneous. Testing cycles, release freezes, and dependency chains all slow down remediation. During this window, attackers continue to scan and probe.
This is where runtime protection and managed WAAP/WAF controls play a critical role:
- Detecting malformed RSC payloads
- Blocking exploit attempts targeting deserialization vulnerabilities
- Shielding applications while patches are validated and rolled out
Layered defense helps organizations stay protected even as vulnerability disclosures evolve.
AppTrana Coverage for React RSC Vulnerabilities
AppTrana WAAP provides validated protection against React RSC vulnerabilities, including CVE-2025-55182, CVE-2025-55183, CVE-2025-55184, and CVE-2025-67779. AppTrana WAF successfully intercepted malicious RSC traffic designed to exploit unsafe deserialization logic, excessive object depth, cyclic data references, and prototype pollution–style manipulation.
By blocking these attack patterns, AppTrana prevented exploitation attempts aimed at remote code execution, denial-of-service scenarios, and server-side source code exposure, all without the need for custom rule creation or manual tuning.
This demonstrates that AppTrana’s built-in behavioral analysis and structural payload inspection mechanisms deliver robust protection against evolving React RSC exploitation techniques, even during active patching and remediation cycles.
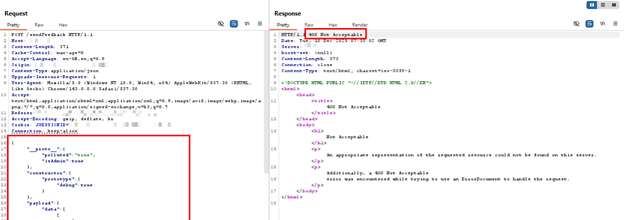
PoC of a DoS-triggering RSC payload for CVE-2025-55184, blocked by AppTrana.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 December 17, 2025
December 17, 2025



