React2Shell(CVE-2025-55182): Critical RCE Vulnerability in React Server Components and Next.js
The modern JavaScript ecosystem was shaken this week as Meta, Vercel, Google Cloud, AWS, and leading security researchers revealed two critical issues: CVE-2025-55182 and the downstream Next.js variant CVE-2025-66478. Both are rated CVSS 10 and allow remote code execution (RCE) by exploiting weaknesses in the React Server Components (RSC) “Flight” protocol. The vulnerabilities affect React 19 and all major frameworks embedding the RSC implementation, most notably Next.js 15.x and 16.x.
Within hours of disclosure, cloud telemetry from AWS MadPot and Wiz Research confirmed active exploitation in the wild, including attempts by China-nexus threat groups such as Earth Lamia and Jackpot Panda. With a weaponized proof-of-concept (PoC) now publicly available, organizations must treat this as an emergency patching event.
What Is CVE-2025-55182 (React2Shell)?
Risk Analysis
Severity: CRITICAL
CVSSv3.1: Base Score: 10.1 CRITICAL
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
Exploit available in public: Yes
Exploit complexity: Low
CVE-2025-55182 is a critical unauthenticated RCE vulnerability in React Server Components. It arises from unsafe deserialization logic in how RSC processes inbound “Flight” payloads.
Under default configurations, an attacker can send a specially crafted HTTP request that manipulates server execution flow, resulting in arbitrary JavaScript execution on the server, even when the application does not explicitly use server functions.
This phenomenon mirrors other historic deserialization vulnerabilities such as Log4Shell or various Java serialization flaws, but React2Shell is even more severe in one key way: it impacts default configurations in mainstream JavaScript frameworks. A simple Next.js project created using create-next-app and deployed without any custom modifications can be exploited.
Importantly, the application does not need to directly use server functions. Simply supporting React Server Components is enough to open the door to exploitation.
Inside the React2Shell Exploit Chain: How Attackers Achieve High-Fidelity RCE
To understand the exploit, we need to look at how React Server Components serialize and deserialize component structures using the RSC “Flight” protocol.
The Key Flaw: Trusting Untrusted Input
The RSC protocol expects a very specific, structured format. In vulnerable versions, the server:
- Receives a serialized Flight payload from the client.
- Does not sufficiently validate the structure or type of data within the payload.
- Attempts to reconstruct component instances and their dependencies.
- Treats attacker-controlled data as part of internal rendering or execution steps.
- Executes code paths that were never intended to be externally triggered.
This enables a well-crafted payload to break out of intended data boundaries and trigger arbitrary execution.
Why Unsafe Deserialization Leads to RCE
Security researchers who discovered the vulnerability reported:
- A near 100% success rate in controlled environments
- The vulnerability’s ability to reach deep into server logic
- The fact that it works even without registering server functions
This is not a fragile exploit that depends on edge-case configurations. It is a reliable, attacker-favored vulnerability with universal reach across the ecosystem.
CVE-2025-66478: Downstream Impact on Next.js
While CVE-2025-55182 originates in React’s decoding logic, CVE-2025-66478 tracks the downstream effect of the same flaw within the Next.js App Router architecture. Next.js directly relies on the Flight protocol to process Server Components, Server Actions, and serialized component data.
Because the vulnerable decoding logic implicitly expands object properties without validation, a crafted Flight payload can inject prototype-polluting keys (e.g., __proto__, constructor). Once these keys are processed inside Next.js, they corrupt core server-side structures and can redirect execution paths toward attacker-controlled code. As a result, unauthenticated RCE becomes possible in default App Router deployments, even when developers have not exposed custom server endpoints.
Mitigating React2Shell: Immediate Steps to Secure React and Next.js Environments
1. Update Frameworks That Bundle React Server Components
To fully remediate CVE-2025-55182, organizations must upgrade React to the patched versions (19.0.1, 19.1.2, or 19.2.1) and update all frameworks that bundle React Server Components, including Next.js, which has released fixes in versions 15.0.5, 15.1.9, 15.2.6, 15.3.6, 15.4.8, 15.5.7, and 16.0.7
Also ensure that any other RSC-enabled frameworks or ecosystem projects are updated to their latest patched releases, as all implementations may be potentially impacted.
2. Apply WAF Protections
A WAF helps by blocking malformed RSC Flight payloads that attempt unsafe deserialization and reducing the risk of exploitation while patches are applied and preventing attacker-crafted payloads from ever reaching your application.
3. Inventory All React and Next.js Deployments
Organizations should locate:
- Public-facing Next.js applications
- Internal services built on React RSC
- Container images embedding vulnerable builds
- Deployed artifacts on CI/CD pipelines that may not have been updated
In large enterprises, legacy build artifacts often linger in production long after code repositories have been patched.
4. Monitor for Indicators of Exploitation
Key signals include:
- Unusual RSC payload structures in logs
- High-frequency malformed requests
- Consistent probing from the same IP ranges
- System commands appearing in logs
- Suspicious file writes in temporary directories
Given the scale of scanning already occurring, organizations should assume attempts are inevitable.
How AppTrana WAAP Blocks React2Shell Exploitation Attempts
AppTrana WAAP provides immediate protection during patch windows by detecting and blocking malicious RSC Flight payloads designed to exploit CVE-2025-55182 and CVE-2025-66478. Its advanced request inspection engine analyzes serialized Flight protocol data, atypical component structures, manipulated JSON fragments, and abnormal parameter patterns that attackers use to inject execution-level inputs into vulnerable React and Next.js servers.
By intercepting these malformed or suspicious RSC payloads before they reach the backend, AppTrana prevents execution of attacker-controlled JavaScript, blocking attempts to run system commands, access sensitive files, or compromise server processes.
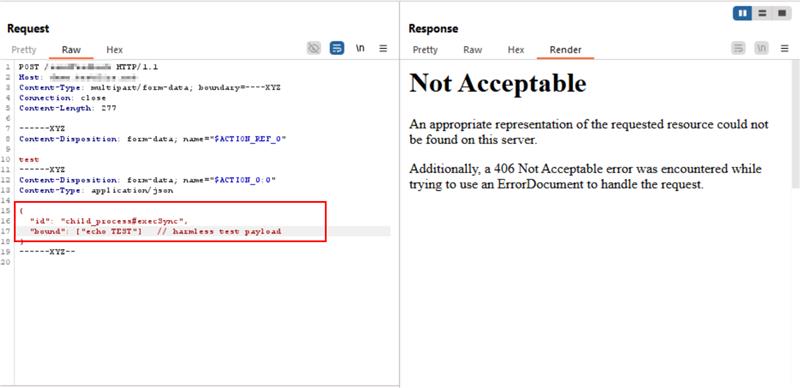
The following example demonstrates how AppTrana mitigates exploitation attempts linked to CVE-2025-55182 and CVE-2025-66478 :
CVE-2025-55182

CVE-2025-66478
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 December 5, 2025
December 5, 2025



