CVE-2025-54057: Stored XSS Vulnerability in Apache SkyWalking Exposes Monitoring Dashboards to Attackers
Apache SkyWalking is one of the most widely adopted open-source Application Performance Monitoring (APM) and observability platforms, trusted by developers and DevOps teams to visualize telemetry, trace distributed systems, and ensure application uptime.
However, a recently disclosed vulnerability has revealed that the very dashboards designed to improve visibility could be turned into attack vectors.
The vulnerability CVE-2025-54057, poses a serious risk to organizations using SkyWalking to monitor sensitive or mission-critical environments.
What Is CVE-2025-54057?
CVE-2025-54057 is a stored cross-site scripting (XSS) vulnerability caused by improper neutralization of script-related HTML tags in the SkyWalking web interface.
In SkyWalking, malicious tags can be injected into content that later renders on dashboards or detail pages without proper sanitization. When those pages are viewed by administrators or operators, the attacker’s code executes automatically.
| CVE ID | Description | Severity | Affected Versions | Fixed Version |
|---|---|---|---|---|
| CVE-2025-54057 | Stored XSS vulnerability in SkyWalking web interface | Important | All versions through 10.2.0 | 10.3.0 and later |
How CVE-2025-54057 Works
CVE-2025-54057 exploitation does not require complex techniques; only the ability to submit or manipulate data that ends up rendered on SkyWalking’s dashboards.
Step-by-Step Attack Flow
- Injection – An attacker submits crafted input containing a malicious script such as <script> or event-based payloads into any data flow that is rendered by the UI (for example, logs, traces, or fields linked to monitored entities).
- Persistence -The payload is stored in SkyWalking’s backend database.
- Execution -When another user opens the affected dashboard or detail page, the malicious code executes automatically in the victim’s browser context.
- Impact– The script runs with the same privileges as legitimate application code, allowing attackers to steal data or manipulate sessions.
Why CVE-2025-54057 Is Dangerous
While XSS vulnerabilities are not uncommon in web applications, stored XSS represents one of the highest-risk variants, especially within administrative tools like observability dashboards.
This threat level arises because:
Automatic Execution
Once injected, the malicious code executes every time a user visits the page; no user interactions such as clicking links or submitting forms are needed. Merely loading the dashboard triggers the attack.
No Ongoing Attacker Presence
The attacker only needs one successful injection.
After that:
- The attack persists indefinitely.
- No command-and-control sessions are required.
- Detection becomes more difficult since execution is triggered via normal page viewing.
Potential Impact of CVE-2025-54057
If CVE-2025-54057 were successfully exploited within an Apache SkyWalking deployment, the impact would extend far beyond a simple dashboard defacement incident.
- Credential Theft: Malicious scripts can steal usernames, passwords, session cookies, and OAuth/API tokens, enabling attackers to log into SkyWalking directly, move laterally across connected systems, and maintain persistent unauthorized access.
- User Impersonation: Hijacked sessions let attackers act as legitimate admins, change configurations, disable alerts, and delete logs or traces to hide malicious activity.
- Monitoring Data Manipulation: Attackers can inject fake metrics, suppress real error logs, and mask outages, misleading response teams and delaying remediation.
- Sensitive Data Leakage: Exposed dashboards can leak PII, transaction data, API endpoints, and infrastructure details, leading to privacy violations and compliance risks.
- Lateral & Supply-Chain Risk A compromised dashboard can be used to access deployment credentials, tamper with pipelines, pivot into backend systems, and trigger wider enterprise breaches.
Steps to Mitigate the Apache SkyWalking XSS Vulnerability
To protect your environment from potential exploitation of CVE-2025-54057, organizations should immediately implement the following mitigation measures:
- Upgrade immediately to Apache SkyWalking version 10.3.0 or later (only official fix).
- Verify the active version through the dashboard or release configuration to confirm the patch is applied.
- Audit dashboards and logs for any suspicious script injections or abnormal entries.
- Rotate credentials and API tokens, especially for high-privilege and administrative accounts.
- Invalidate active sessions to prevent continued use of potentially stolen session cookies.
- Monitor platform activity closely for unusual logins, configuration changes, or telemetry modifications.
- Perform a security review to identify any lateral movement or data exposure prior to patching.
CVE-2025-54057: AppTrana WAAP Coverage
AppTrana WAAP protects against CVE-2025-54057 by detecting and blocking malicious script injections used in stored XSS attacks. It analyzes request parameters, payloads, and encoded inputs to stop JavaScript and HTML injection attempts before they reach SkyWalking dashboards, preventing credential theft and session abuse.
The following example shows how AppTrana mitigates exploitation attempts linked to CVE-2025-54057:
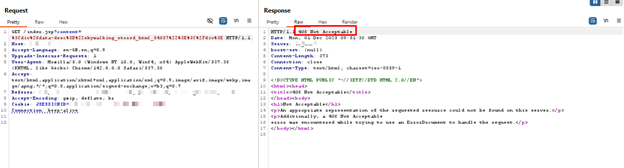
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.


 December 2, 2025
December 2, 2025



