Apache Commons Text Code Injection Vulnerability (CVE-2025-46295)
A critical code injection vulnerability has been identified in Apache Commons Text, a widely used Java library for text processing and interpolation. Tracked as CVE-2025-46295, the vulnerability carries a CVSS v3 score of 9.8 (Critical) and affects all versions of the library prior to 1.10.0.
The vulnerability has an EPSS score of 0.253%, indicating a low short-term probability of exploitation. However, Apache Commons Text is deeply embedded across thousands of Java applications, frameworks, and enterprise products, making this a significant supply-chain risk with potentially severe impact if left unaddressed.
What is CVE-2025-46295?
Risk Analysis
Severity: CRITICAL
CVSSv3.1: Base Score: 9.8 CRITICAL
Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Exploit available in public: No
Exploit complexity: Low
Affected Versions: Apache Commons Text < 1.10.0
The vulnerability exists in Apache Commons Text’s interpolation functionality, which replaces placeholders in text strings at runtime. In older versions, certain interpolators were overly powerful and could execute system commands or access external resources.
If an application passes untrusted input directly into these interpolation APIs, attackers can inject specially crafted expressions that evaluate attacker-controlled expressions and may lead to code execution depending on the application context.
Apache Commons Text is not a niche component. It is widely distributed across Java ecosystems, often bundled within frameworks and third-party software.
A vulnerability in such a dependency creates supply-chain exposure, where a single unpatched library can introduce risk across multiple applications and environments. This makes timely remediation critical, even in the absence of widespread exploitation.
CVE-2025-46295: Root Cause of the Code Injection Vulnerability
The vulnerability resides in Apache Commons Text’s interpolation functionality, which replaces variables and expressions inside text strings at runtime.
In versions prior to 1.10.0, certain interpolation features were overly permissive. When applications passed untrusted input into the text substitution API, attackers could craft malicious expressions that triggered unsafe interpolators capable of:
- Executing system commands
- Accessing external resources
- Evaluating unintended expressions
This improper control over code generation enables remote code execution when vulnerable input paths are exposed.
CVE-2025-46295: Why Remote Code Execution Is High Risk
Remote code execution vulnerabilities are among the most severe security risks because they allow attackers to execute arbitrary commands with the privileges of the affected application.
If exploited, CVE-2025-46295 could enable attackers to:
- Access or exfiltrate sensitive data
- Modify application behavior or data
- Deploy malware or backdoors
- Disrupt service availability
- Move laterally within the environment
The vulnerability has low attack complexity and requires no privileges, increasing the potential impact in exposed environments.
CVE-2025-46295: Remediation and Risk Reduction Steps
Organizations should take prompt action to reduce exposure to CVE-2025-46295 and prevent potential remote code execution.
- Upgrade Apache Commons Text – Immediately upgrade to version 1.10.0 or later, which removes the unsafe interpolation behavior. For full coverage and long-term stability, upgrading to the latest version 1.15.0 (released December 2025) is strongly recommended.
- Audit Direct and Transitive Dependencies – Review applications and third-party software to identify both direct and indirect (transitive) usage of Apache Commons Text. Many affected environments may be exposed through embedded frameworks or vendor products.
- Restrict Untrusted Input Usage– Ensure that user-controlled or external input is never passed directly into text interpolation or substitution APIs without strict validation and sanitization.
- Disable or Limit Risky Interpolation Features– Where possible, remove or restrict advanced interpolation options that allow expression evaluation, command execution, or external lookups.
- Monitor Application Logs and Runtime Behavior– Actively review logs for signs of abnormal activity, such as unexpected command execution, outbound connections, or unusual runtime errors that may indicate exploitation attempts.
AppTrana Coverage for Apache Commons Text Code Injection (CVE-2025-46295)
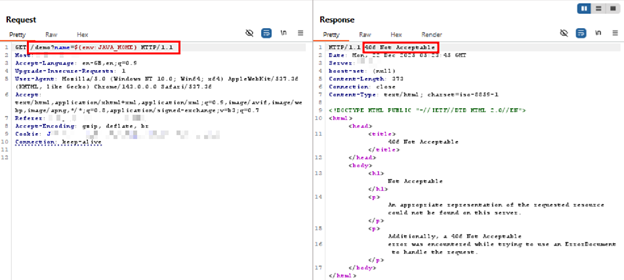
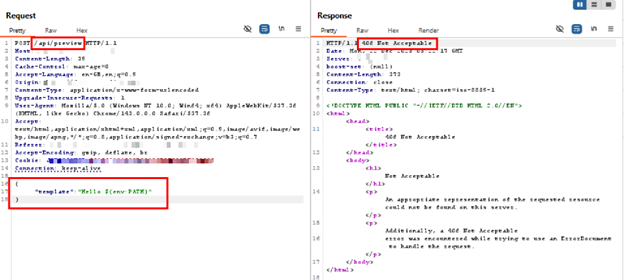
AppTrana WAAP detects and blocks expression-based injection attempts associated with CVE-2025-46295 at the HTTP layer, even when the vulnerable Apache Commons Text library is not directly exposed. Detection is performed by inspecting request bodies for anomalous expression patterns before they reach backend interpolation APIs.
The block confirms that non-destructive payloads still reveal the exact exploitation mechanism that could lead to remote code execution if passed into vulnerable text substitution functions. This demonstrates AppTrana’s defense-in-depth protection, providing effective coverage during patching and remediation cycles without requiring custom rules.
Screenshots showing expression-based injection attempts associated with CVE-2025-46295, detected and blocked by AppTrana WAAP at the HTTP layer.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 December 23, 2025
December 23, 2025



