What is WAAP? – A Quick Walk Through
Many of the businesses that already have revenue-generating web applications are starting an API-first program. Now, old monolithic apps are being broken into microservices developed in elastic and flexible service-mesh architecture.
The common question most organizations grapple with is – how to enhance application security designed for web apps to APIs and API security?
Protecting APIs against modern cyber threats requires going beyond the traditional solutions. Web Application and API protection (WAAP), the next generation of Web Application Firewall (WAF) comes to the rescue.
What is WAAP?
WAAP (Web Application and API Protection) is a set of cloud-based security services specially designed to protect web applications and APIs. This security tool is far more advanced than a WAF that mostly monitors OWASP application threats. This expanded WAF integrates, observes, and takes intuitive action when needed. With real-time logs and statistics, it can integrate well with other applications the company uses.
WAAP Vs WAF
A Web application firewall (WAF) is specifically intended to protect web applications by monitoring and filtering web traffic, and blocking unauthorized or malicious traffic. In contrast, WAAP solution incorporates WAF and API security to provide a more comprehensive defense against web application and API attacks.
Challenges in securing web applications and APIs
APIs are not insecure by nature, but due to the complexity and quantity of API adoption, it is easy to have security gaps and cyber risks waiting to leap out. Without proper functions, security testing, authentication checks, and input validation, APIs can become a perfect target. Hackers just need one loophole for a successful exploit.
1. API Security Breaches are Piling Up
- In addition, the IBM Security X-Force report highlighted that two-third of all cloud breach incidents are now involved in misconfigured APIs.
- API has emerged as a major actor vector with many companies reporting API-related security breaches. For example, Pelton, a fitness company exposed three million customer data due to a flawed API, which allows access to a private account without proper authentication.
- Venmo, USPS’ Corporate Database Exposure, Facebook’s Breaches, and JustDial are a few other companies that experienced API security attacks.
These growing threats drove the need for a new platform with API-specific security features outside the scope of traditional security management tools. This is simply an extension of the requirement for VLANs, firewalls, RASPs, and WAFs.
2. Traditional Security Solutions Are No Longer Enough
Enterprises must meet several requirements to maintain their web application and API protection levels. Unfortunately, the traditional security solutions that most enterprises usually deploy create problems rather than providing solutions.
False Negative Vulnerability Scanning
If you are scanning APIs with a general web application scanner, then you are most likely missing 8 out of 10 API vulnerabilities. A vulnerability scanner that was not designed to catch API vulnerabilities will result in false-negative reports. As a result of the lack of findings, they suggest that your APIs are secure. However, it is more likely that the scanner didn’t scan for any API weaknesses.
API Gateway Security Limit
The API gateway provides various security functionalities for authenticating API users, rate limiting, audit trail, and ensuring compliance. Though it offers basic API protections, it leaves many opportunities for attackers. The API gateway concentrates only on the front door of the API. The security can be compromised by fake and compromised credentials.
Signature-based Solutions are Insufficient for API Security
Signature-based approaches are based on the analysis of the previous attack. However, when a new attack happens, which does not match with the signature, the tools won’t stop it. Further, the signatures and static rules can’t prevent business logic attacks as the traffic looks legitimate. Broken Object Level Authorization (BOLA), this business logic vulnerability occupies the number one position in the OWASP Top 10 API Threats list.
WAFs – Static Rules Fall Short
WAFs (Web Application Firewalls) prevent attacks by allowing only safe traffic through the web applications. A Web Application Firewall is an important part of AppSec, but there are some limitations with its static rule-based protection. The continuous change in modern web apps and APIs requires manual tuning as well as rule development – making manual administration a prerequisite.
Traditional WAFs that focus on the attacks originating from external traffic might leave the insider attacks undetected.
RASP (Runtime Application Self-Protection) – Patterns are Misleading
The visibility of RASP is limited when it needs to be engaged with microservices at different endpoints. Though it stops the attack against these endpoints, it can’t detect actions across the entire service at once. In addition, as it does not learn the business context, it may predict a valid use case as an attempt to attack and stop it.
Demands Inspection of Encrypted Traffic
While TLS encryption denies the ability of hackers to surveil the traffic, it makes the traffic content invisible to the firewall for inspection. It offers intruders a great way to hide anything they want to add to the stream using security technologies.
Core Capabilities of WAAP Solutions
As firewalls and other security solutions are no longer enough to fulfill the API security compliance requirements, the way to address this situation is to adopt a consolidated platform called WAAP.
WAAP evolved as a product suite and provides comprehensive security solutions for monolithic and microservice-based apps as well as APIs. It ensures protection against known and zero-day attacks with an integrated WAF, anti-DDoS, bot management, and API protection.
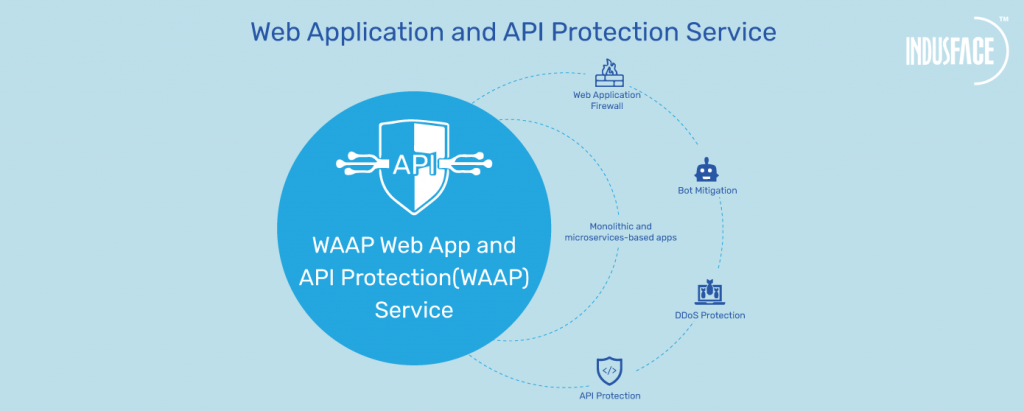
WAAP: Core Capabilities
Fully Managed WAF (Web Application Firewall)
A fully managed, cloud-based WAF serves as the first line of defense for defending web applications and APIs. They supplement the signature-based protections offered by IPS and firewalls.
One of the primary actions that WAFs use to detect and prevent attacks is the ability to deny requests based on specific criteria.
For example, AppTrana WAF uses reputation databases such as Spamhaus DB and HoneyPot project to blacklist malicious IPs and block requests from those sources. Geolocation-based blocking using MaxMind DB is another technique that can deny access to prevent attacks.
By monitoring apps’ behaviors and usage and through deep inspections, the Web Application Firewall designs a baseline of normal app behaviors. Then, the WAF can trigger actions when anomalies arise in the cloud or the data center.
A fully managed WAF solution can also ensure defenses against the OWASP Top 10 vulnerabilities, DDoS attacks, malicious sources, and complex threats targeting web apps and APIs, including buffer overflow, SQL injection, file inclusion, XSS, cookie poisoning, and many others. Learn more about how does a WAF work, here.
API Security
Automated API protection shields API endpoints from exploitation. It comprises a wide range of functions like monitoring and logging, traffic management, and API versioning. Further API protection includes additional essential security features such as authorization and authentication, rate limiting, API key verification, and call rewriting. API security also includes dynamic attack signatures to detect threats targeting APIs.
Bot Mitigation and Management
Malicious botnets are a key tool for initiating an attack against an API. Bot mitigation capabilities block malicious bot activity while allowing bots that support legitimate business needs like search engines or performance and health monitoring tools. With seamless visibility as well as control over bot traffic, it protects websites, web applications, and APIs from automated traffic.
DDoS Attack Protection
Anti-DDoS solutions secure on-premise as well as cloud-based assets no matter where they’re hosted (Microsoft Azure, AWS, or Google Cloud). WAAP ensures that its DDoS mitigation strategy is capable to detect and mitigate API-focused distributed denial of service attacks. It blocks traffic at the edge for seamless business continuity with no performance impact and guaranteed uptime.
Additional WAAP Capabilities
ML-Based Threat Detection
Signature-based detection contributes to many false positives. WAAP employs ML-based threat detection to defend against zero-day attacks with a minimum of false positives.
Real-Time Attack Analytics
The Web application and API protection tool offers complete visibility with domain expertise and employs ML techniques to monitor all security events and reveal attack patterns.
Automation And Orchestration
In addition to the core capabilities, web application and API protection solutions offer automation and enable orchestration across the entire infrastructure. Manually creating rules and rewriting policies can’t keep up with the pace of innovation. WAAP approach automates the flow of security events and empowers incident response workflows.
Adopting this unified solution can bring operational benefits through automated rule updates. The WAAP solution’s built-in intelligence enables it to learn independently and adapt to the ever-changing threat landscape.
Choosing The Right WAAP Solution
A Web Application Firewall (WAAP) is a critical component of any organization’s security infrastructure, designed to protect against a wide range of web application and API attacks.
While the importance of a WAAP cannot be understated, not all WAAPs are created equal. Therefore, evaluating and choosing the best WAAP for your organization is essential. To assist you in this process, we have prepared an informative article on cloud WAF pricing that highlights key considerations.
Here are some key factors to consider when evaluating WAAPs:
Security Effectiveness
The most important factor to consider when evaluating WAAPs is their security effectiveness. Look for a solution that provides comprehensive security features such as web application firewall, DDoS protection, bot protection, and vulnerability scanning.
A WAAP should be able to effectively identify and block all application and API attacks while allowing legitimate traffic. It should be able to detect zero-day vulnerabilities and continuously update its security rules to protect against new threats. To evaluate WAAP’s effectiveness, organizations should perform security testing against it using different attack scenarios to see how it responds.
Ease of Use
Another crucial factor to consider is the ease of use of the WAAP. The WAAP should be easy to configure, manage, and maintain. It should have a user-friendly interface allowing security teams to identify and respond to security incidents quickly. Moreover, it should integrate with other security tools and workflows so that security teams can streamline their processes and workflows.
Customization
Your web application and API are unique, and your security solution should reflect that. Look for a service that allows customization and configuration to meet your requirements. The service should also provide granular control over security policies and rules, allowing you to fine-tune the level of protection for different components of your application.
Reporting and Analytics
A good WAAP should provide detailed reports and analytics that help organizations to understand their web application traffic and identify potential vulnerabilities. WAAP should be able to provide actionable insights that allow security teams to prioritize their efforts effectively.
Compliance
A WAAP should be able to help organizations to comply with regulatory requirements such as the Payment Card Industry Data Security Standard (PCI-DSS), the General Data Protection Regulation (GDPR), and other security standards. It should provide features such as log retention, compliance reporting, and audit trials to help organizations demonstrate compliance.
Cost
Organizations should choose a WAAP that provides the best value for their money. The cost of a WAAP should be proportional to its security effectiveness, scalability, and ease of use. Moreover, organizations should consider the total cost of ownership (TCO) of the WAAP, including acquisition, implementation, and maintenance costs.
Performance
Your security service should not impact the performance of your web application or API. Look for a solution that provides fast and efficient protection without affecting the response time of your application. The security solution should also be scalable to handle traffic spikes and increasing volumes of data.
Support and Maintenance
Look for a solution provider who provides 24/7 support and maintenance. They should offer regular updates and patches to protect against new security threats. The provider should also provide training and documentation to help you understand and configure the security settings.
AppTrana WAAP Solution
AppTrana WAAP offers comprehensive application and API protection that effectively safeguards against various threats and vulnerabilities, including those identified in the OWASP Top 10 web and API threats list. With an advanced multi-layered approach, AppTrana protects against the known threats, Zero-day vulnerabilities, and more without disturbing the performance of the applications.
It combines web application firewall, API security, bot mitigation, and DDoS protection technologies into one easy-to-use solution.
Our Web Application and API Protection identifies anomalous behavior, distinguishes benign traffic from the malicious one. Furthermore, it provides customized protection for each app without requiring time-consuming manual tuning.
Moreover, the platform utilizes a positive security model based on HTTP industry standards and coding best practices, thereby ensuring proper application behavior.
Indusface has earned global recognition on the Gartner Peer Insights Voice of the Customer Cloud WAAP report as a Customers’ Choice. It is the only vendor with a 100% recommendation rating for three consecutive years, highlighting its outstanding performance.
The Gartner Peer Insights Customers’ Choice recognition is granted to vendors and products that receive high ratings from their customers across four distinct categories:
- Product Capabilities
- Deployment experience
- Sales experience
- Support experience
Download complete report here.
With WAAP, you can eliminate threats before they get in, keep hackers out of your system, and more. Secure your business and protect your reputation with the advanced WAAP solution!
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 March 29, 2023
March 29, 2023






