Top 6 DDoS Attack Prevention Tactics 2021
The hundreds of billions of insecure devices, especially IoT products out there mean it is simple for attackers to develop botnets. Over the past years, DDoS (Distributed Denial of Service) attacks are being used maliciously. The attack has hit HSBC, Bitcoin, Sony, and PayPal along with several other organizations.
The continuing growth of number, range, and type of DDoS attacks, making the best DDoS protection and mitigation a crucial security to-do in the IT’s security list.
The first blog in our DDoS series highlighted the best practices for DDoS prevention. If you are privileged enough to have endured an attack or simply strategic enough to plan ahead – here we will address the top tactics of DDoS protection 2021.
What are DDoS Attacks?
In a Distributed Denial of Service attacks, cybercriminals target web services or websites intending to disrupt and overwhelm them. Attackers generate the traffic through hundreds of thousands of botnets from servers, PCS, and other internet-connected devices towards the targeted systems, to the extent that they’re taken offline. A DDoS attack can last for seconds, hours, or even days and block the victim’s online service available to legitimate users.
DDoS Attacks Are Intensified In 2020
The ongoing COVID-19 pandemic makes more people rely on online services and this has been reflected in the DDoS market as well. A new threat intelligence report by NetScout highlights exactly what is happening – the attackers launched more DDoS attacks in 2020 than ever before. It is observed that 4,83 million DDoS attacks in 2020 up to a 15% increase if compared to 2019.
Further, Kaspersky observed a direct rise in the duration of the DDoS attacks.
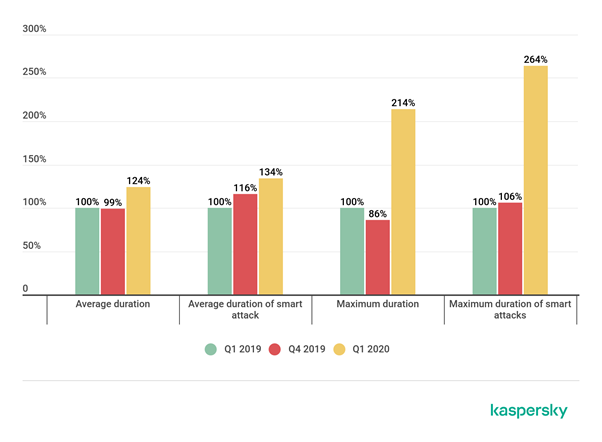
The main reason that DDoS attack prevention is challenging is that most of these attacks are amplification attacks, which involve sending small packets to the victim, which then respond with larger packets to the targeted server, which is under attack.
The increase in size and complexity fits in the DDoS trends, which have been striking for several years. For example – the chart depicts the significant increase in the size and complexity of DDoS attacks in 2019 compared to 2018.
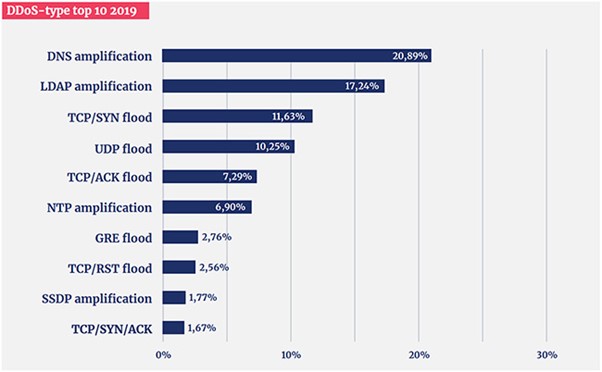
Image Source: Helpnetsecurity
Challenges of DDoS Attacks
In DDoS attacks, attackers repeatedly check the target’s system security to ensure their attack achieves the major damage. The attack begins by exploiting a vulnerability in the system and then spreads via malware, progressively shutting down the system and making the site inoperable.
As malicious traffic can come from hundreds or thousands or even millions of IP addresses, it is hard to detect the attacking devices. Further, the tools to launch DDoS attacks are available in a few dollars while the cost to the attacked organization can range from $20,000 to $50,000 per hour. There are various types of DDoS attacks, including layer 3 – 4 and 7 attacks, DNS attacks, peer-to-peer attacks, ICMP flooding, and SYN flooding.
Large-scale attacks have severe financial consequences for businesses all over the world. Businesses not only risk losing sales and traffic but are incapable to access critical tools, which they require in their everyday operations. Although the best DDoS protection and mitigation solutions are available, it might not be simple for small organizations with fewer resources.
Top Tactics for DDoS Attack Prevention 2021
With the best DDoS protection strategies prepared in advance, companies won’t be caught up in the unguarded moment. To avoid becoming the victim of a DDoS attack, take these DDoS prevention measures:
1. Assume You Are A Target Regardless of How Small You Are
Many SMBs think that DDoS attackers target only large corporations, the government, and banks and they will never be the target. As a result, they don’t take proper precautions against the attacks.
The reason for a DDoS attack could be anything, including a protest against organization policies, an extortion attempt, or even an act of ex-employee revenge.
Every business has a measurable ROI associated with their online presence and anybody can feel the pain from their service being overwhelmed as a target.
You should always consider what your web host providers’ security policies are regarding DDoS protection and ensure that they’re adequate to defend your site against high-volume DDoS attacks.
Get URI-Based DDoS Protection for your Applications
2. Don’t Rely on A Traditional Firewall
Even traditional firewalls claim to have built-in anti-DDoS capabilities, they’ve only one method of DDoS blocking – the practice of indiscriminate thresholds, which blocks the particular port when its maximum threshold limit is reached. Cybercriminals aware this is an ideal way to block both legitimate and malicious users. As the application and network availability is affected, the end goal is achieved.
3. Adopt Off-Premise Cloud-Based Solutions
While traditional firewalls provide only network layer protection, cloud-based solutions equipped with additional filtering capabilities are vital to defending against application-layer attacks. Cloud-based Web Application Firewalls (WAF) are not limited by the uplink limitation, ensuring virtual scalability as they’re deployed outside your network.
Further, the off-premise cloud-based mitigation solutions are managed services, and won’t demand investment in maintenance. This cost-effective solution provides better protection against application and network layer threats. You can enable the cloud-based DDoS protection solution either as always-on or on-demand services with industry-leading security vendors.
On-demand cloud DDoS attack prevention stops network layer attacks like UDP floods and SYN floods that are volumetric attacks built to block network pipes with forged data packets. The always-on option is powerful enough to stop application layer attacks attempting to initiate TCP connections with an app to drain server resources. This option prevents attacks like DNS floods, HTTP floods, and low-and-slow attacks.
While choosing a cloud-based DDoS prevention solution, be sure to look for real-time security event logs and reporting along with automatic threat mitigation.
4. Log Monitoring and Analysis
You might wonder how to stop DDoS attacks with log monitoring. In fact, it is the best way for the rapid detection of DDoS threats because of the data and statistics they offer regarding your web traffic. Log files contain data with ample information efficient to detect threats in real-time.
Using log analysis tools to detect DDoS threats accompany other benefits like making the DDoS remediation process fast and easy. While listing the statistics of your site traffic, they indicate the date and time of huge spikes in the traffic as well as which servers have been affected by the attack. The log analyses can save you time by reducing the troubleshooting time by pre-informing the state of unwanted events. Few intelligent log management tools also provide you with the information required to quickly remedied and mitigate the damages of a successful DDoS attack.
5. Prepare DDoS Resiliency Plan
The business should realize that defending from DDoS attacks doesn’t limit prevention and mitigation. As the DDoS attack intends to shut down your complete operation, most anti-DDoS protections are majorly concerned with bashing the attack down. Keep the practice of disaster recovery planning as a part of your regular operational maintenance.
The plan should focus on technical competencies and a comprehensive plan, which outlines how to ensure business continuity under the pressure of a successful DDoS attack.
A disaster recovery site must be a part of your resiliency plan. The DR site which serves as the temporary site should have a current backup of your data. The recovery plan should also comprise critical details like what the recovery approach is, where critical data backups are maintained and who is accountable for which tasks.
6. Ensure Security Through Compartmentalization
Security experts also strongly advise security compartmentalization for the most vulnerable resources. Maintain separation of privileges to those who have access to the network – entry-level employees no need to have access to proprietary secrets. With network compartmentalization, you can ensure that your most important resource won’t be taken down by a DDoS attack.
Conclusion
DDoS attackers are becoming more powerful; so, you should change the DDoS protection tactics. Go beyond the basic security strategy to detect and remediate vulnerabilities in your system and network, constantly monitor your network traffic, prepare for a DDoS breach, and connect with the managed security providers to stay on top of the recent threats and mitigation solutions.
You can start with the AppTrana Free Forever Website Security Scan to find out how it works.

 December 2, 2020
December 2, 2020






