OWASP Top 10 Vulnerabilities
With this OWASP top 10 vulnerabilities educative series on the web and mobile applications, we aim to break down vulnerabilities and simplify them to the basic level of their nature and implications with examples and illustrations.
OWASP Top 10 Vulnerabilities
Once there was a small fishing business run by Frank Fantastic in the great city of Randomland. He happily named it the Fishery of Randomland. After years of struggle, it grew more than he could imagine and then he decided to come up with a website and mobile app.
Wasn’t it the best of ideas? His customers could just order fish from anywhere. They didn’t even need to visit the store anymore. Frank was happy until he discovered something fishy. His money was evaporating from the website. Every day, there were unexplained transactions and charges.
“How is this happening,” he asked a few of his employees who had no clue about it. They just noticed fraudulent transactions and data being stolen from computers.
Frank was furious but couldn’t just shut the website down as it was now the source of most of their operations. Losing money was not an option either.
Find such security issues on your website with Free Website Security Scan.
So, one fine day Frank decided to hire a security expert from the suburbs of the Randomland. His name was ‘Ralph’ and he ran a web security firm in the town. Here’s what Ralph told Frank about the website that Fishery of Randomland should have known earlier.

You may want to explore OWASP Top 10 Vulnerabilities in 2021: How to Mitigate Them?
A1- Injection
“It is the most serious weakness that is compromising your data and overall security,” said Ralph to Frank. He pulled out the account login page and entered a string of code.
Apparently, the command was accepted and allowed him to login without even a valid account or password.

This is an injection attack.
Simply put, if you are not filtering user inputs correctly, hackers can use commands to enter through this hole and claim legitimate access. Surprisingly, they can use anything from sign-in forms to the comments box and send commands to the server.
Business Risks: Think of unlimited possibilities when hackers have a direct way of interacting with your server. They can steal data, change it, delete it, deny access, and so much more. In fact, injection attacks such as SQL Injection are allegedly responsible for major data breaches at Ashley Madison and Sony.
A2- Broken Authentication and Session Management
Once Frank and his team understood the Injection risks, Ralph moved on to a different method of bypassing security on Fishery of Randomland. He asked for a valid account ID and tried to log in it with a random password.
“Why does the message say that password is incorrect and not the ID,” he asked Frank.
“We want to help customers know that they have used a wrong password,” he answered hesitantly.
“And you are also helping a brute force attacker know that an account does exist. He only needs the right password,” said Ralph.
He went on to explain how negligence in customer accounts, password recovery, and even sessions can lead to increased security risks. Surprisingly, when he closed the browser window and reopened it again, the website still allowed him to continue using the account. Ralph suggested using Web Application Scanning to keep an eye on such vulnerabilities.
It all falls under broken authentication and session management.
Business Risks: Such vulnerabilities allow an attacker to claim complete account access. In severe cases of the attack, hackers have stolen database records and sold them to the underground black market.
A3- Cross-Site Scripting(XSS)
Apparently, it is the most common OWASP top 10 vulnerabilities and Fishery of Randomland’s website had this one too. With this Cross-Site Scripting weakness or XSS, attackers could use web applications to send a malicious script to a user’s browser. This is what makes XSS even more dreadful; it poses a threat to both users and the website. Hackers basically intercept communication between server and browser to inject malicious codes at both ends.
“If you are not separating trusted data from untrusted data, you deserve to be hacked,” Ralph got serious on finding multiple vulnerabilities.
He emphasized the fact that XSS not only harms the website but also allows attacks to redirect users on any other URL. Think of it this way, a customer uses the link for Fishery of Randomland’s website to purchase fish but instead of their actual site, hackers send them to Fishery of Fraudland. Now, this website might look and feel real but all the data exchanged is going to the hacker. If a customer is cheated this way, he will blame Frank for the rest of his life and badmouth about it too.
“They come on your website thinking that it’s a safe world, they get redirected and hacked, they never trust you again. What’s worse is that they talk about it with everyone,” he concluded XSS.
Business Risks: Hackers can change the homepage of the website and write something like ‘Hacked by XYZ group’. They can even inject malware on the site that usually leads to getting blocked by search engines and browsers.
A4- Insecure Direct Object References
“Here’s a trick now,” Ralph said to Frank while changing a few numbers in the URL carefully and pressed enter.
Apparently, Fishery of Randomland was showing internal account IDs, which were their parameters to recognize different accounts. Ralph simply changed the last digit there and the website took him to the transactions page for another account.

That’s Insecure Direct Object Reference vulnerability and it allowed Ralph to access unprivileged data because the numbers were predictable. It does not just account numbers. Actually, there can be multiple predictable patterns that will allow hackers to get into the database and access restricted data.
Business Risks: Though there are not many changes an attacker can make, there is a lot that he can access and expose. Attackers can view credit card details, address and phone numbers for other customers, and even previous transactions.
A5- Security Misconfiguration
Misconfigured security is a tough vulnerability to handle as it takes into account all security lapses at every level of the application. The fishery of Randomland had to have this vulnerability given their scarce security knowledge and Ralph wasn’t surprised at this one.
“Old sample apps, unnecessary features, default system passwords, hackers love all the additional information they can get. And you have plenty of it,” he said.
Ralph was right. Most system admins ignore changing their passwords or even disabling ports and accounts they do not use anymore. Attackers look for such small lapses, combine them, and try to make something big out of it.
Business Risks: If used cleverly, OWASP security misconfiguration can lead to complete loss of data through alteration, deletion, and theft. Attackers can use one vulnerability after the other to access the database.
A6- Sensitive Data Exposure
“How secure is your data,” asked Ralph.
“What data?” hesitant Frank replied. There was so much going around that he wasn’t sure of anything now.
“Everything. Data is sent to the users, your backups, password logs, everything,” he probably knew the answer but asked anyway.
Judging by the lack of confidence around, Ralph guessed that encryption wasn’t a priority at Fishery of Randomland. So, he went back to the computer, which apparently had more answers.
Unsurprisingly, Frank’s team was storing user passwords, credit card details, and other pieces of critical information in pure text files.
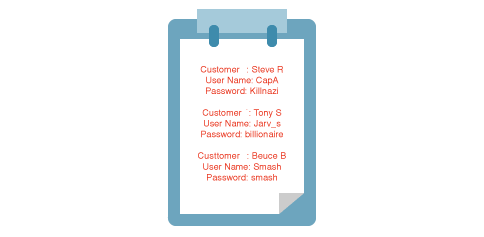
“La force dun secret,” he turned back and said as everyone looked amazed, “It’s French for ‘The Strength of a Secret’. If you don’t know the language, what is said is of no use to you.”
Frank and his website admin team were uncertain if he was being sarcastic or simply playful.
“That’s how you should store or transmit the data. Encrypt it, obviously not in French but with cryptographic algorithms. Even if the passwords or credit card details are stolen, make sure that hackers cannot do anything with it,” he cleared the point.
It’s critical to keep the data encrypted in such a way that only authorized keys or algorithms unlock it.
Business Risks: Consider everything that comes with the loss of sensitive data. Loss of passwords, credit card information, addresses, and bank statements might bring serious repercussions. Recently, Uber accidentally revealed driving licenses for more than 100 drivers.
A7- Missing Function Level Access Control
“Admin function controls are the most important ones and should be restricted. Right? What if non-admin users can access it too? Do you regularly check for these misconfigurations? Make sure that you do,” he explained further.
Ralph’s question reveals a lot. Most companies do not bother reassuring that only authorized accounts access privileged information. What if someone with network-level access can change privileges or URLs?
Business Risks: Once the attacker gains admin access, he/she can change a lot of things including application data and settings.
A8- Cross-Site Request Forgery (CSRF)
“Here’s a malicious link is hidden in an image that your customer visits on a random website,” Ralph typed in his notepad.
While “rfish” is the real website for Fishery of Randomland, fraudsters have altered the URL for the customer to initiate a command that he/she doesn’t even know about.
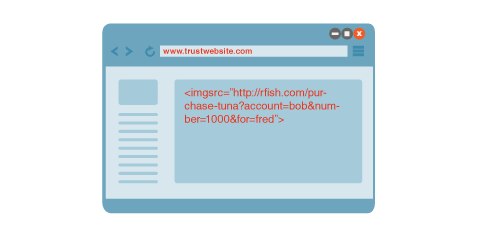
<img src=”http://rfish.com/purchase-tuna?account=bob&number=1000&for=Fred“>
“Now your customer doesn’t even know but the attacker has initiated a transaction of 1000 tunas to be delivered to Fred. Every time he visits such a malicious website, similar requests will be passed to your website with all the authenticated details,” Ralph revealed a much serious flaw.
“You mean all those customer complaints about random orders were real? God, they hate us,” frustrated Frank pulled a chair hoping that it was the end of bad things on his website but of course it wasn’t.
Business Risks: Rogue requests, purchases, and money transfer. You will never be sure if it’s genuine requests and customers will gradually lose trust in your website.
A9- Using Components with Known Vulnerabilities
“Hey Frank, what happens when you mix unknown construction material while building a house,” Ralph wasn’t finished yet.
“Well, it might not be strong enough? Who knows what’s in there?”
“Exactly my friend. Applications are the same. Your developers use open source projects with God knows what loopholes. Most of the time they don’t even know what code library came from where,” he explained.
Business Risks: Unknown application codes bring unknown risks. XSS, injection risks, and business logic loopholes are just some of the examples. Such vulnerability brings data breach, access control, defacement, and theft risks.
A10- Unvalidated Redirects and Forwards
“Coming to the last one; this is another weakness where you lose customer trust,” Ralph said as he pulled the keyboard to show how it was easy to plant a spam redirect in the URL to take the customer to a page of his choice. He simply used the ‘URL’ parameter to change it as explained in the example below.
“See now that the customer has clicked on the link but does not know that I am taking him to a website that looks exactly like yours but it isn’t. He will go about his business while I can get all the information I need,” Ralph concluded.
Most websites don’t even know about such unauthorized redirects that look genuine. While customers should be more careful about phishing, how could someone suspect that they’ll be redirected to gettingrobbed.com that looks exactly like rfish.com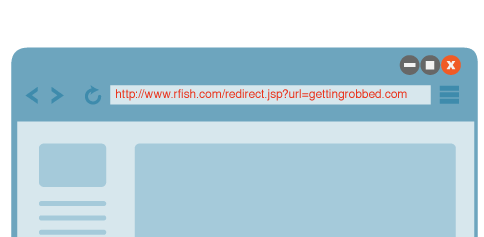
http://www.rfish.com/redirect.jsp?url=gettingrobbed.com
It comes down to website owners to ensure that the customer is not redirected to frauds by restricting and controlling URL parameters.
Business Risks: Attackers can install malware or access user accounts with phishing. Customers lose trust in the attacked website forever.
OWASP Top 10 Vulnerabilities Resolution
“Ralph, that’s like a list of thousand variables. You want us to look at it every day and crosscheck if everything is fine with the website? How about I just close everything and sell fish at my shop in Downtown,” Frank wasn’t sure of his website anymore.
“Not at all,” Ralph smiled, “I know you people have a business to take care of and that’s why we have things that check every weakness on your website.”
“Things?”
“Well, back in the office we call them Web Application Scanning
“And what do they do exactly?”
“See this Web Application Scanning has parameters to find OWASP top 10 vulnerabilities weaknesses automatically. It does that day and lets you know issues to be taken care of. That’s obviously better than your development team digging in every single day,”
“And this firewall? We already have that right Bob?” Frank looked at one of his employees.
“No, no it’s different. This Web Application Firewall is for OWASP top 10 vulnerabilities. Say you find three weaknesses through scanning and at the same time it’s the big sale day on your website. What will be your priority? Should your team sit and correct the code or focus on keeping the website running? Web Application Firewall prevents OWASP top 10 web attacks until you can fix the issue,” Ralph cleared the difference.
Find out all the OWASP top 10 vulnerabilities and SANS vulnerabilities on your website with a Free Forever Website Scan.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 October 16, 2019
October 16, 2019






