How to Stop a DDoS Attack?
“Imagine your website is a store, Distributed Denial of Service (DDoS) is like a mob in front of your store that doesn’t let your customers get in. It’s an unpleasant situation having tens of thousands of fake shoppers eating up your valuable resources, all at once.” Know how to stop DDoS attacks.
DDoS has emerged as a huge problem for businesses across the world. Hackers use this attack by overwhelming traffic and victimizing critical web resources, which eventually makes the server unavailable to satisfy genuine requests. The rent-a-bot services, offering fake traffic at as low as $5 an hour, virtually put every business at the risk of an attack.
Take a look at some recent findings that provide a glimpse into the lethality of a DDoS attack.
- DDoS attacks cost banks up to $100, 000 per hour.
- 20% of such attacks last for days and even months.
- 87% of the attacked companies were hit more than once.
- 13% more DDoS attacks in 2021 than in 2019
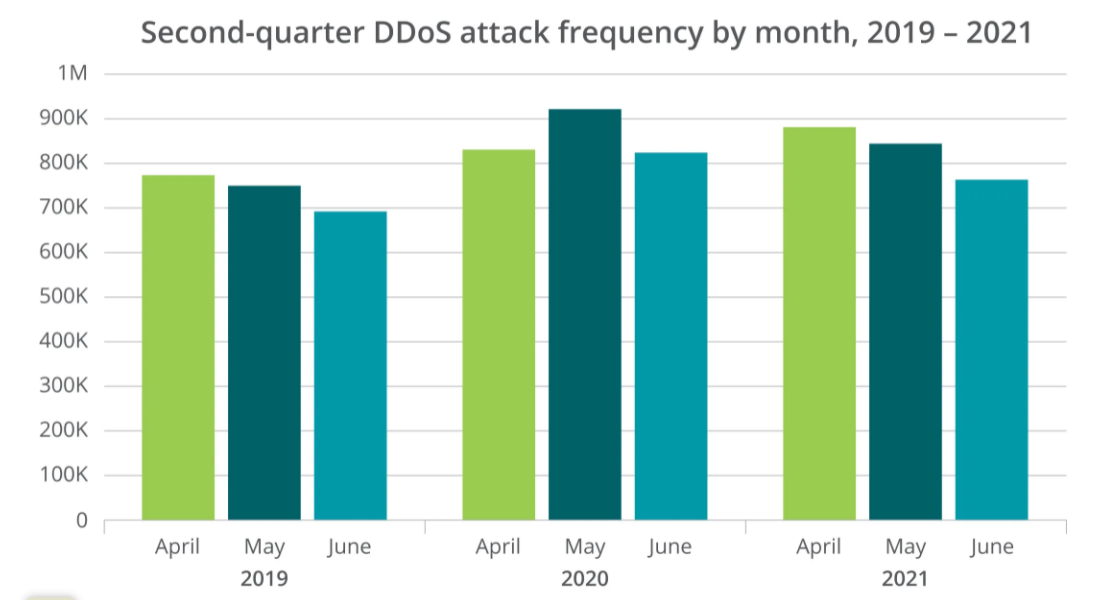
Source: Netscout
Regardless of the business you’re in, keeping a business application up and running is critical to your brand’s reputation, and hackers want to exploit this weakness with DDoS attacks. The unpredictability of these attacks makes it difficult to prepare for them, which further incentivizes criminals to take action.
Let’s learn more about the problem, and how your business and data centers can defend against DDoS attacks. Also if you’d like to test a website for risks, start with AppTrana Free Trial.
What Are the Types of DDoS Attacks?
1. Volume-based DDoS attacks
This is a classic type of DDoS attack, which exercises a massive amount of traffic to overwhelm bandwidth and makes it impossible for valid traffic to flow in and out of the victim site. Attackers carry out this volumetric DDoS attack to completely saturate the target’s network capacity.
2. Protocol-based Attacks
These types of DDoS attacks are built to consume the processing capacity of network resources like firewalls, servers, and load balancers by focusing on Layer 3 and 4 protocol communications with mischievous connection requests. In this attack, the packets are created to make communicating servers wait for a non-existing response during a normal handshake protocol.
3. Application-based Attacks
Most of the sophisticated attacks involve the exploitation of vulnerabilities in the application layer – Layer 7. There is no exception for the DDoS attack as well. In these types of DDoS attacks, hackers use weaknesses in the application software or web server software, which leads the server to crash or hang. The most standard type of application DDoS attack involves initiating partial requests to a server to consume finite resources and make the entire DB connection pool busy so that it can jam legitimate requests.
There are ample sub-types of attacks, which fall into either one of these common types of DDoS protection but show unique characteristics. Some of the popular DDoS attack methods are:
- SYN Flood
- SYN-ACK Flood
- LAND attack
- ACK & PUSH ACK Flood
- Fragmented ACK Flood
- Spoofed Session Flood (Fake Session Attack)
- UDP Flood
- VoIP Flood
- DNS Flood
- NTP Flood (NTP Amplification)
- SSDP Flood
- SNMP Flood (SNMP Amplification)
- CHARGEN Flood
- Misused Application Attack
- ICMP Flood
- Smurf Attack
- Slowloris
- Zero-Day DDoS
How to Stop DDoS Attacks?
Step 1: Understand That Every Business Is Vulnerable
The frontline of defense in DDoS protection is understanding how vulnerable your business is.
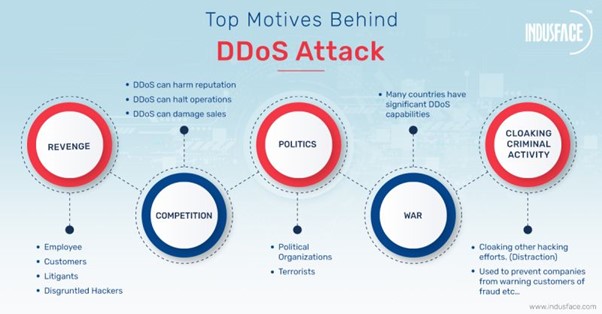
While many DDoS attacks are motivated by revenge, politics, trolling, and terrorism, money is frequently involved. According to cybersecurity analysts, ransom and blackmail are the most common motives behind DDoS attacks. Hackers disrupt web services and hold them against a ransom. Hackers ask for heavy ransom amounts, which when paid, leads to the attack being stopped and services made available to customers.
Similarly, competition motivates people to bring down better-performing rivals while revenge from disgruntled employees leaves a similar impact. Politics, terrorism, war, and diversion techniques cloaking some other hacking attempts are also common reasons for carrying out application DDoS attacks.
Primary Attack Motivation:
Step 2: Deploy Protection Tools
Network DDoS: Network layer DDoS attacks try to exploit the network by sending in more data packets than what a server can handle, or abusing bandwidth beyond the network port’s ability. These are often reported in media due to their record-breaking volumes.
Application DDoS: On the other hand, application-layer attacks are more silent and smaller in volume but cause far more damage. Since most companies deploy their resources on the cloud, hackers now explore attack options beyond the network layer.
“These attacks are also more prevalent due to lower resource requirement. For instance, an application on Amazon Web Services (AWS) can process SYN flooding of up to 200,000 packets (‘elastic bandwidth costs’ is a different discussion altogether). However, the same AWS server instance can be brought down by a meagre 500 HTTP requests per second when the application runs on CMS (Joomla or WordPress).”
Do you see the difference? 500 HTTP requests per second is a cheaper attack to execute.
More sophisticated Layer 7 DDoS attacks not only bring down the server but aid in data breaches too. In such an attack, California State University at Sacramento lost 1800 social security and driver’s license numbers from its staff. Attackers used multiple compromised systems to trick the DNS server into leaking the authentication security code.
Deploying WAF is one of the best DDoS attack prevention methods.
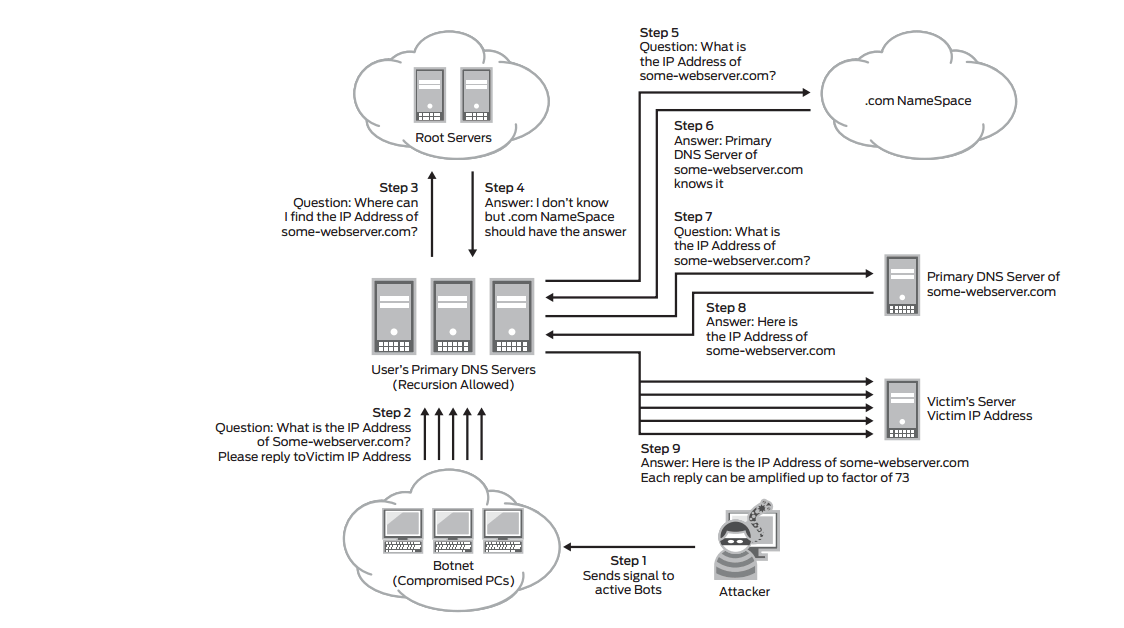
What is a web application firewall?
A web application firewall is the best protection against the most common types of application DDoS attacks. Yet, complete automation doesn’t offer the best network security. Managed Web Application Firewall(WAF) screens Layer 7 traffic and feeds data directly to cybersecurity experts who can recognize malicious chunks of traffic trying to bring your services down. Once known, they apply rules and policies to block such attacks based on bot signatures, malicious IPs, and so on. It helps you stop DDoS attacks effectively.
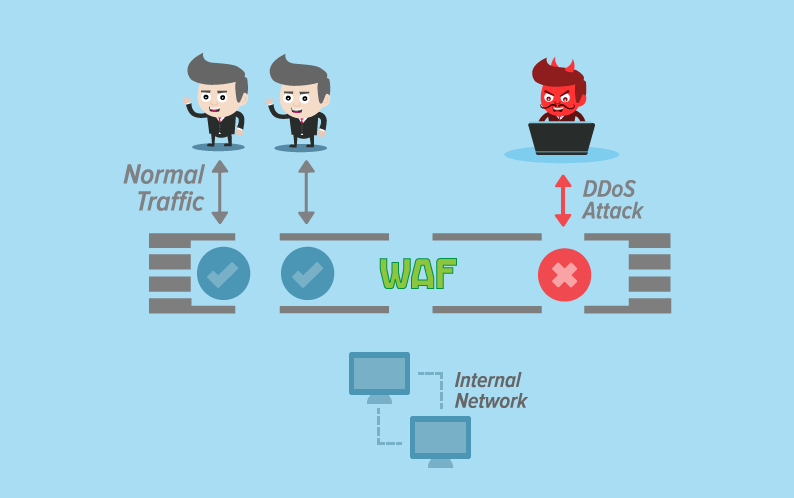
Step 3: Monitor Application Traffic Continuously
Nothing can prepare your business to detect and prevent DDoS attacks better than continuous monitoring. Security experts can distinguish sudden spikes in traffic from bot traffic. Eventually, such monitoring delivers actionable data on attack vectors to define DDoS protection policies.
An application layer distributed denial of service attack is initiated by hiring machines, bots, or by taking control of remote systems. These components are used for generating fake requests to a targeted server. With such a large number of fake requests, cyber criminals try to make the services of an application or server unavailable for hours, days or weeks. A successful DDoS attack can eat huge chunks of the bandwidth, processing speed, and memory to slow down and/or disrupt applications.
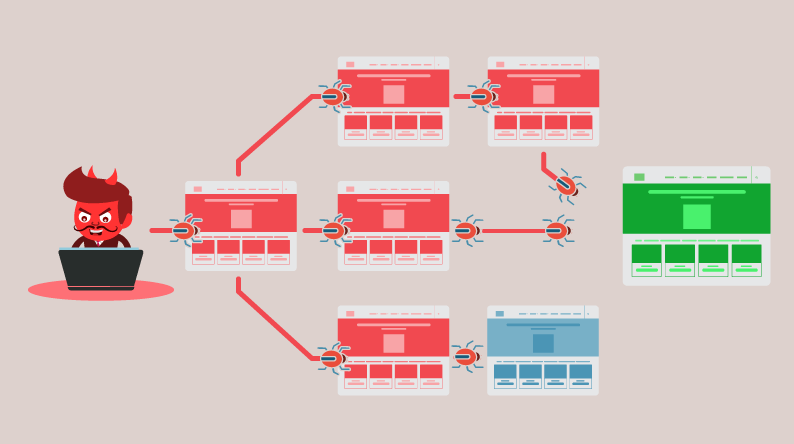
The ease of availability makes an application layer DDoS attack more lethal than a similar network layer attack. Anyone can purchase the custom-coded DDoS module and launch it on any desired web application. In fact, with a little knowledge of underground markets, a basic DDoS attack will not cost the perpetrator more than a few hundred dollars. While there are different types of sophisticated DDoS attacks, this is the most common.
When compared to the network layer DDoS, application DDoS is much easier to execute. It requires lower computing power and fewer systems, which still leads to catastrophic results (a primary reason why application DDoS is becoming more prevalent).
Take the Slowloris attack for example. Slowloris was originally created to show how a single machine could keep multiple connections open simultaneously for long periods, ultimately crashing the server. Slowloris has become more sophisticated over time, and still just requires up to a few machines (that generate several thousand requests each) to cause a server to run out of connection pools and crash – making it a huge threat.
Think Application Layer
Application vulnerability exploits that trigger application distributed denial of service are also worth a mention here. Several honeypot operations have shown that attackers can exploit BASH vulnerability to plant malware bots that accept multiple commands including UDP, JUNK, and TCP flood to carry DDoS. Likewise, there is a myriad of other application vulnerabilities that can be exploited to facilitate attacks.
When it comes to DDoS attack prevention and DDoS mitigation, there is no silver bullet technology that can solve every problem. With multiple trajectories of attack, ongoing attack methods, and zero-day vulnerabilities, automated technology alone is bound to fail. It cannot protect against multiple threats while also ensuring legitimate traffic doesn’t suffer. That is where human experience and decision-making skills come in. Continuous expert monitoring with actionable insights is the most effective combination to stop DDoS attacks and ensure security that can prepare organizations with a proactive defense strategy.
Step 4: Inhouse DDoS Security or Managed App Security
You can hire and train security professionals with Layer 7 experience to stop DDoS attacks and other application security risks in-house. A dedicated team can monitor attacks and take actions efficiently.
However, with the shortage of experienced cybersecurity workforce and massive costs involved in hiring and managing such teams, new businesses invest in managed application security vendors to stop DDoS attacks. Such a team not only offers 24 × 7 traffic monitoring and DDoS attack mitigation but complete application security including:
- Latest security notification to protect your applications from known vulnerabilities.
- Periodic penetration testing.
- Business logic tests on all applications to find vulnerabilities, zero-day threats, and automated application risks.
- Custom WAF rules to block attacks (via virtual patching).
- Tracking the malicious behavior of an attacker initially versus simply blocking the attack.
- 24/7 monitoring to gather information such as IP address, User ID if authenticated, GEO location, navigation/user behavior, and machine fingerprint that can help gain intel about the attacker’s methodologies to use that information in creating more aggressive blocking rules from these attackers.
How vulnerable is your website to DDoS attacks? Follow the above-mentioned DDoS prevention steps to secure your website and stay ahead of hackers.
Join 47000+ Security Leaders
Get weekly tips on blocking ransomware, DDoS and bot attacks and Zero-day threats.

 April 3, 2018
April 3, 2018






