DDoS Mitigation – Why Your Traditional Security Fails?
If you look around, even a small successful DDoS attack brought down websites. It leads to data breaches and results in a huge loss. DDoS attacks on AWS (in 2020), Bandwidth.com (in 2021), and GitHub (in 2018) carry a lesson for us.
DDoS attacks are among the most rapidly advancing type of cybercrime. It becomes more mature, sophisticated, and complex.
In 2023, Cisco predicted the total number of DDoS attacks would be over 15 million.
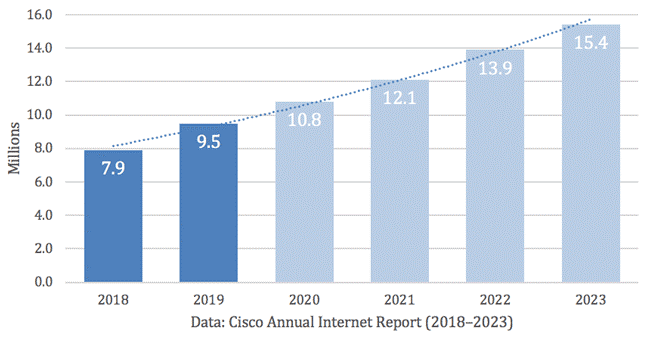
If the threat is evolving, you must evolve with advanced security solutions. Traditional DDoS mitigation is not enough to counter these attacks. Why is it so, and what is the way forward?
Not sure if it is an attack? Review the common DDoS symptoms here
The Constant Evolution of DDoS Attacks
There is confusion and disagreement about the first recorded DDoS attack. It is believed that the first DDoS attack was against the University of Minnesota in 1999.
Yet others believe it was in 1996 against Panix, an ISP in New York. In either case, the threat has been around for over 2 decades.
In the Panix attack, the SYN flood overwhelmed network resources. It blocked Panix from processing legitimate requests for close to 36 hours.
In the University of Minnesota attack, a network of 114 computers was infected with the malicious Trin00 script. Here the malware sent large volumes of data packets to overwhelm the server.
In 2000, a Canadian teenager orchestrated a string of DDoS against big corporations like Amazon, eBay, FIFA, Yahoo, and CNN.
Then, DDoS attacks were leveraged for cyber-vandalism, hacktivism, and state-sponsored cyberwarfare.
Today, there is a rise in ransom DDoS wherein attackers block access to the systems until huge ransoms are paid. There have been several high-profile ransom DDoS incidents in recent years.
Businesses are also using DDoS as an unethical business competitive strategy. Here, enterprises use DDoS-for-hire services to make the competitor’s online services unavailable. This destroys the reputation of the competitors. Also, divert traffic away from their websites and cause financial losses.
3 Reasons Why Traditional DDoS Mitigation Fails
1. The Server-Class Botnet-Powered DDoS Attacks
In the previous decade, DDoS attacks peaked at 15 Gbps. However, the size of volumetric attacks has grown over the past 10-12 years. We have witnessed attacks that reached a size of over 2 Tbps.
Attackers can keep increasing the size of DDoS due to the availability of vulnerable IoT devices. In 2021, they can also bring high-powered servers and high-capacity network devices into botnets.
Your traditional denial of service mitigation often depends on blackhole routing, built-in redundancies, CDN, and firewall to prevent attacks.
These protections can stop IoT botnets from controlling spoofed traffic. But the high-powered server-class botnets can easily bypass these defenses.
Only flexible, reliable security solutions can protect against such attacks. It is equipped with in-built failovers, security expertise, and infrastructural strength.
2. The Growing Sophistication of DDoS
There is a sharp increase in the number of application-layer attacks. Further, the low-and-slow attacks are often less than 1 GB in size but are equally lethal. There is also a manifold increase in multivector attacks and highly evasive encryption attacks.
Usually, distributed denial of service mitigation solutions deploys cloud-based WAFs at the network edge to counter these attacks. You need to fine-tune these solutions to protect against advanced DDoS attacks,
To this end, security experts must back the solution. They should understand this ever-evolving threat and contextual intelligence about your IT infrastructure.
3. The Reducing Duration of Attacks
The time taken to reach maximum attack bandwidth is just 1.5 minutes. And attacks last for a few minutes today, unlike in the 2000s. Before, the attacks lasted for days and weeks. Despite the shorter duration, attacks are much more vicious today than ever.
Most DDoS mitigation providers do not have the best response times. They tend to protect only against those attack types they know. They cannot detect shorter-duration DDoS attacks in real-time. Also, they can’t minimize the consequences on your organization and resources.
Is a DDoS attack hitting your site right now? Get immediate help
The best DDoS attack mitigation solutions offer always-on, instant protection against all kinds of attacks. They leverage the following features to detect anomalous activities in real time and stop them:
- Real-time traffic monitoring and analytics
- Behavioral and pattern analysis
- Fingerprinting
- Security analytics
- Latest global threat feeds
The Way Forward
The size, frequency, and severity of DDoS attacks are evolving at an accelerated pace. DDoS mitigation cannot be a one-and-done solution. It needs to keep evolving too.
As the traditional solution has limits, choose a solution that can cater to evolving threats. Consider a fully managed, advanced DDoS prevention solution like AppTrana. It ensures adequate and ongoing security.
Stay tuned for more relevant and interesting security articles. Follow Indusface on Facebook, Twitter, and LinkedIn.

 November 3, 2022
November 3, 2022





