DLL Hijacking and How It Is Done?
Windows application comprises various folders and files. These files include executables, DLL and various other formats. A DLL is loaded dynamically and the code of the DLL is only executed by an executable. Many applications nowadays do not verify the integrity and the authenticity of the DLL due to which it becomes quite common for attackers to replace the existing DLL with a DLL crafted with malicious code. This vulnerability is known as DLL hijacking.
The vulnerability arises from the fact that unlike executable files, a malicious DLL is generally not detected by antivirus applications.
Here is the scenario to replicate this issue in a vulnerable application.
First, we need a malicious DLL. Just for demonstration, we are simply using a malicious DLL that shows a popup when the application is vulnerable.
In our case, we are using a vulnerable application named Mezzmo version 5.0.5.0 which is vulnerable to DLL hijacking. We need to identify the vulnerable DLL. One simple way to do that is to try every DLL in the application folder one by one. We tried replacing the file “avcodec-57.dll” with our malicious DLL with the same name
As an attacker, we can do this by creating an executable using WinRAR that extracts the file into the mezzmo directory and replaces the old one. We can create a silent one as shown in the screenshot below.
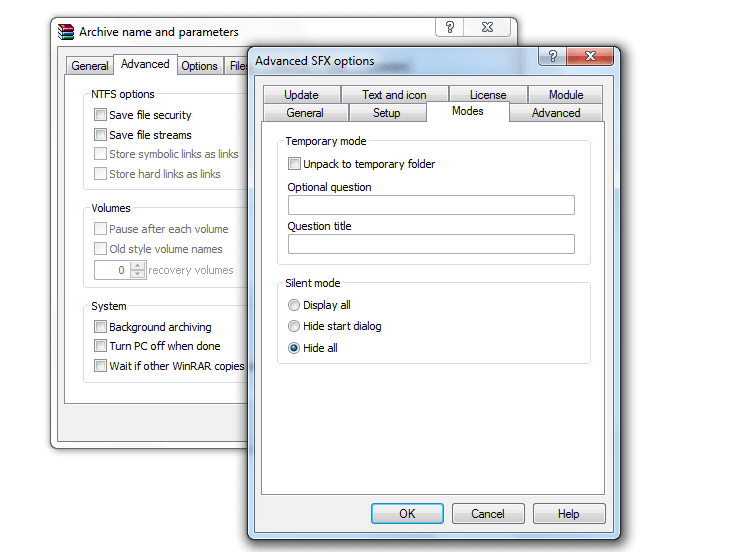
When the mezzmo.exe is executed the DLL also executes as shown in the below screenshot.
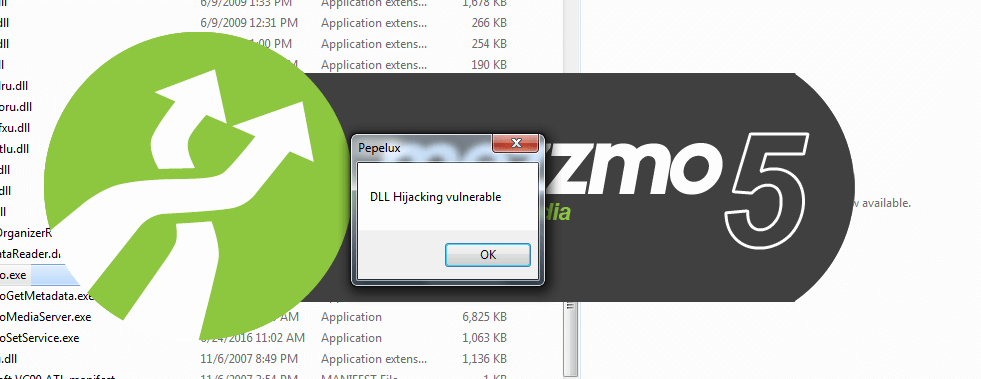
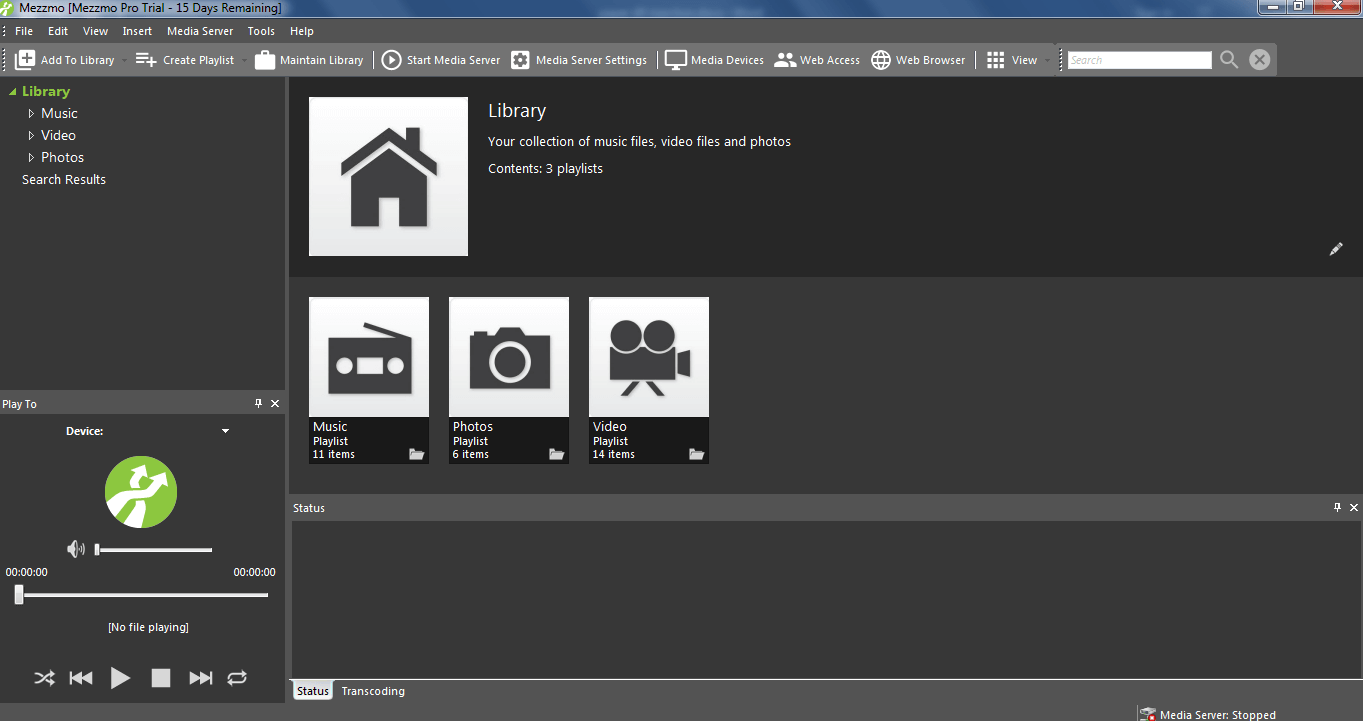
Even after showing us the error the program executes just fine.
In order to actually exploit this issue one can construct a DLL using a Metasploit that will provide us a reverse shell.

 November 10, 2016
November 10, 2016



